Cybersecurity researchers have identified a potential connection between two Yemen-based cybercriminal organizations, the Belsen Group and ZeroSevenGroup, following an extensive investigation into their operational patterns and attack methodologies.
The discovery comes amid growing concerns about sophisticated network intrusion campaigns targeting critical infrastructure and enterprise systems across multiple continents.
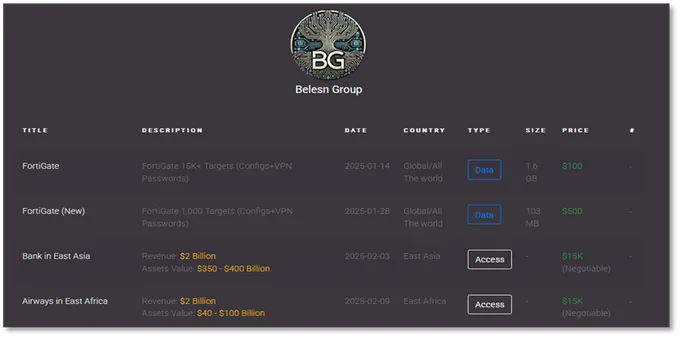
The Belsen Group first emerged in January 2025, making headlines with the leak of 1.6 GB of sensitive data from over 15,000 vulnerable Fortinet FortiGate devices.
The compromised information included IP addresses, system configurations, and VPN credentials, which the group initially shared freely on BreachForums and their dedicated TOR-based blog to establish credibility within cybercriminal communities.
The group’s attack vector centered on exploiting CVE-2022-40684, a critical authentication bypass vulnerability in FortiGate firewalls, suggesting they maintained access to victim systems for over two years before the public disclosure.
ZeroSevenGroup, the more established of the two entities, has been active since July 2024, initially operating on platforms including NulledTo before expanding to BreachForums, CrackedTo, and Leakbase.
The group specialized in data monetization strategies, targeting organizations across Poland, Israel, the United States, UAE, Russia, and Brazil.
Their most notable breach involved Toyota’s US operations in August 2024, where they claimed responsibility for exfiltrating 240GB of sensitive corporate data.
KELA Cyber Team analysts noted significant operational similarities between the groups through forensic analysis of their posting patterns and communication styles.
The investigation revealed that both organizations employed identical title formatting conventions, specifically using “[ Access ]” with square brackets and spaces in their forum posts and victim announcements.
This distinctive formatting pattern was unique to these two actors within KELA’s comprehensive threat intelligence database.
Tactical Convergence and Attribution Analysis
The technical analysis revealed deeper connections through OSINT investigation of the groups’ digital footprints. Researchers identified matching stylistic patterns in their social media presence, particularly consistent hashtag usage including #hack across their Twitter profiles.
Both groups demonstrated similar operational security practices, maintaining multiple communication channels including Tox, XMPP, Telegram, and X for victim negotiations and data sales.
The Belsen Group’s operational infrastructure included a sophisticated onion site for victim listings and contact information, registered under the partially redacted email address [email protected].
Their Telegram administrator account (@BelsenAdmin, ID 6161097506) revealed additional intelligence through subscription patterns to cybersecurity certification groups, regional Arabic-speaking communities in Yemen, and technical training channels.
The account’s previous usernames (@m_kyan0, @mmmkkk000000) provided additional attribution markers for ongoing investigations.
ZeroSevenGroup’s technical profile showed evolution from their earlier incarnation as “ZeroXGroup” on RaidForums under username zerox296.
The group’s password reuse patterns across leaked databases and infostealers provided crucial attribution links, connecting their operations to Yemen-based threat actors associated with the Yemen Shield hacking group.
Their transition to exclusive operations on Exploit Forum since January 2025 demonstrated tactical adaptation following exposure of their scamming activities against the Medusa Ransomware group.
While definitive attribution remains challenging, the convergence of operational patterns, geographic origins, and tactical preferences strongly suggests coordination or shared resources between these cybercriminal entities, representing an evolving threat landscape requiring enhanced defensive measures.
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant Updates.



