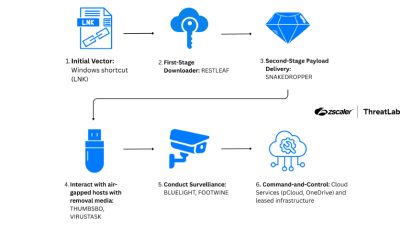
UNC4899 Breached Crypto Firm After Developer AirDropped Trojanized File to Work Device
The North Korean threat actor known as UNC4899 is suspected to be behind a sophisticated cloud compromise campaign targeting a cryptocurrency organization…