researcher StreyPaws has published an in-depth analysis of CVE-2025-38352, a Time-of-Check to Time-of-Use (TOCTOU) race condition in the Linux/Android kernel’s POSIX CPU Timer subsystem. The , disclosed in the September 2025 Android Bulletin, is suspected of being under limited, targeted exploitation.
CVE-2025-38352 arises from improper synchronization in the kernel’s posix-cpu-timers.c file. As StreyPaws explains, “CVE-2025-38352 is a classic TOCTOU (Time-of-Check to Time-of-Use) in the Linux/Android kernel’s Timer Subsystem. Specifically, it arises from a Race Condition in kernel/time/posix-cpu-timers.c.”
The bug can lead to kernel instability, crashes, or unpredictable behavior, and in some cases, may escalate to privilege escalation on vulnerable systems.
POSIX CPU timers track processor time consumed by tasks rather than real-world elapsed time, making them critical for profiling and performance monitoring. According to the research, “Unlike traditional timers that measure elapsed real time, CPU timers monitor how much processing time tasks and processes actually consume, making them invaluable for profiling, resource management, and performance monitoring.”
The system supports multiple clock types: CPUCLOCK_PROF, CPUCLOCK_VIRT, and CPUCLOCK_SCHED, each tailored to different timing needs—from profiling applications to tracking only user-space execution time.
The occurs when two threads interact with CPU timers nearly simultaneously—one handling expired timers, and the other attempting to delete a timer.
StreyPaws writes: “The specific race window occurs … when an exiting task invokes handle_posix_cpu_timers from an interrupt context while, at the same time, another thread attempts to delete a timer using posix_cpu_timer_del. This overlap creates a narrow but critical race condition.”
In essence, the Time of Check (TOC) happens during deletion, when the system verifies whether a timer is firing. The Time of Use (TOU) occurs moments later when the kernel processes the same timer, potentially referencing freed memory. This opens the door to use-after-free scenarios, memory corruption, and system crashes.
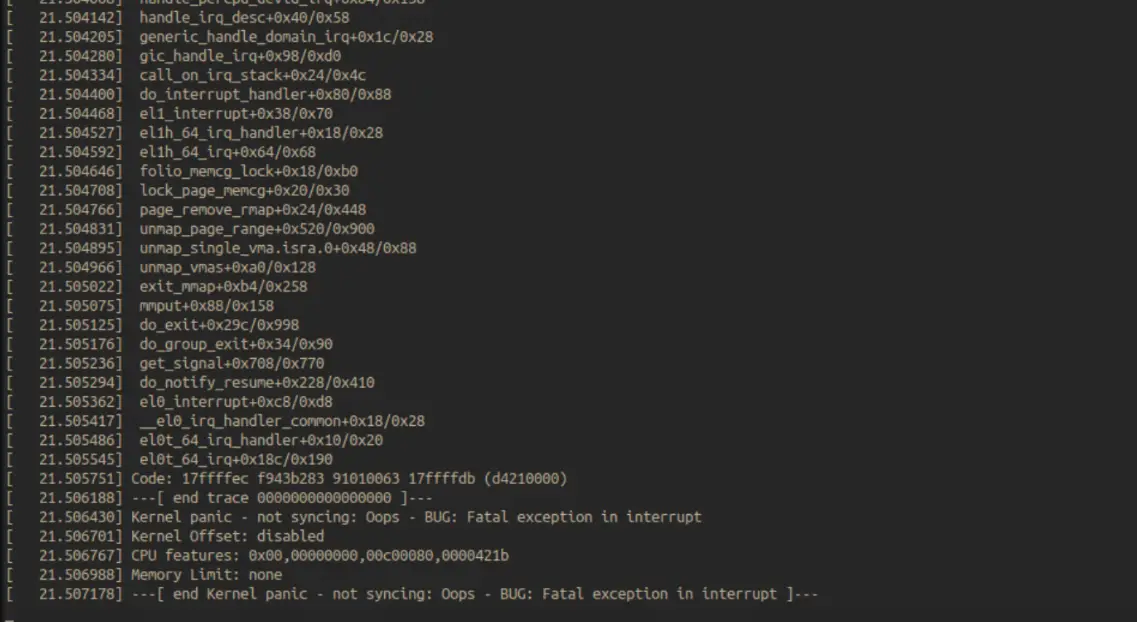
To study the flaw, StreyPaws built an Android kernel emulation environment, reverting the upstream patch to reintroduce the bug. He explains: “Based on the knowledge we gathered so far, I developed a minimal trigger PoC … after a few tries, we get a beautiful crash.”
Even with kernel configurations meant to reduce the risk (CONFIG_POSIX_CPU_TIMERS_TASK_WORK=y), the researcher was still able to force a crash under certain conditions, highlighting the subtle but persistent danger of race conditions.
The kernel patch that addressed CVE-2025-38352 added a simple but crucial safeguard: