The U.S. energy industry has become a prime target for large-scale phishing operations in 2025, according to new research from Hunt Intelligence. The report reveals a sharp increase in look-alike domains designed to impersonate major brands—with Chevron, ConocoPhillips, PBF Energy, and Phillips 66 bearing the brunt of the attacks.
As Hunt notes, “Phishing continues to hit critical industries hard, and in 2025 we’ve tracked a sharp rise in domains built to impersonate major U.S. energy companies.”
Hunt.io data shows growth in brand abuse across the sector:
- Over 1,465 phishing detections against the energy industry in the past year.
- Chevron alone faced 158 impersonating domains in 2025, up from just eight in 2024.
- Many malicious sites slip past detection, with only “1–9 of 94 flagging them, exposing gaps in detection systems.”
Attackers primarily use HTTrack-based cloning to replicate corporate websites, then inject fraudulent login or registration forms to harvest credentials and financial data.
Chevron’s global recognition makes it the most impersonated target. Hunt identified domains such as chevroncvxstocks[.]com and humanenergy-company.com.cargoxpressdelivery[.]com, both cloned with HTTrack and styled with the company’s slogan and favicon.
“The cloned site reproduced Chevron’s branding elements, including its official slogan ‘Human Energy’ and favicon… to strengthen the illusion of legitimacy.”
One of the fake portals even masqueraded as “Chev Corp Stocks”, blending a high-yield investment scam with credential harvesting. Hunt’s analysis revealed that “fraudulent ‘Register’ and ‘Login’ forms were configured to issue POST requests directly to the attacker-controlled server.”
ConocoPhillips was also heavily targeted, with domains like conocophillips.live and conocophils.com. Both were cloned from legitimate content but evaded most security engines.
“The domain conocophils.com was created 11 months ago, has a low detection score, with only 1 out of 94 security vendors flagging it as malicious.”
Another site, xn--conocopillips-2z0g.com, exploited punycode to mimic the company name—highlighting adversaries’ creative use of Unicode tricks to fool end users.
A single domain, advancedownloads[.]com, impersonated PBF Energy, using cloned branding while hiding evidence of development. Investigators found that attackers had staged the phishing kit locally:
“The footer contains a link pointing to file:///C:/Do_Not_Scan/Working/Phishing/3/index.html, which suggests that the attackers developed the page locally in a Windows environment before deploying it.”
Despite the operational slip, the fake site featured an advanced payload delivery system that assembled a malicious ZIP file through chunked Base64 code execution in the victim’s browser.
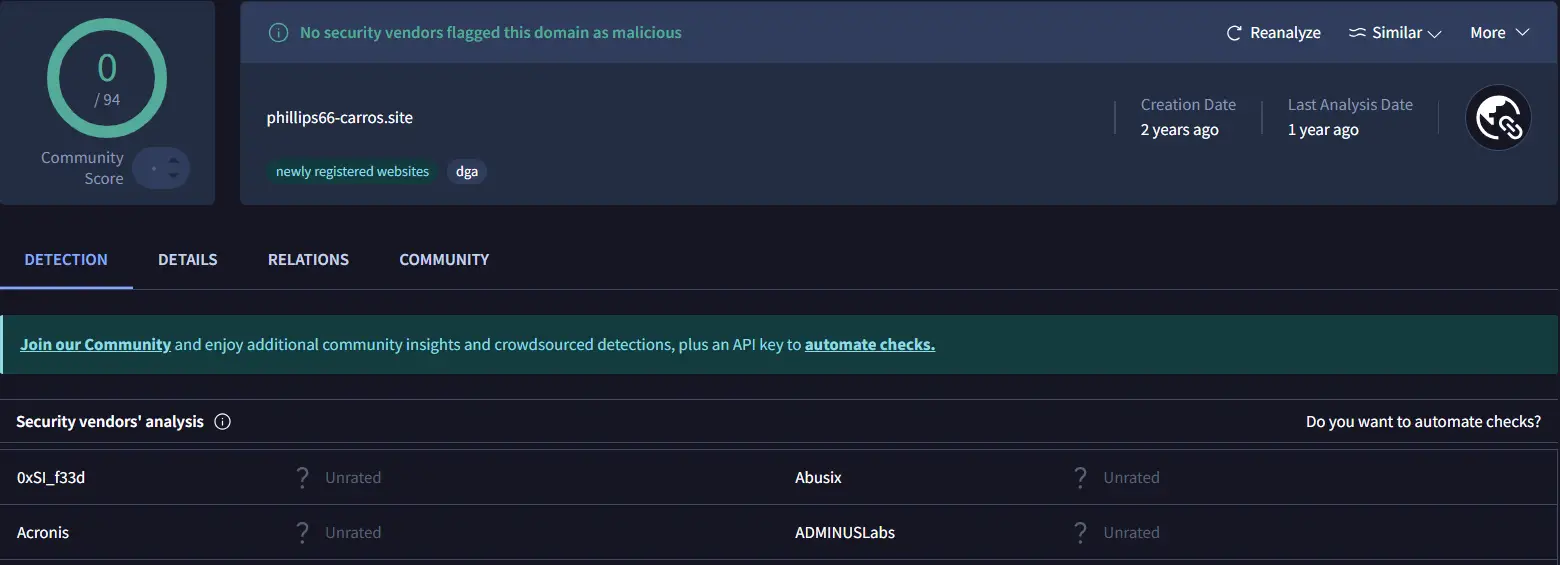
Phillips 66 was targeted with phillips66-carros[.]site, which mimicked the official site but escaped notice entirely. “VirusTotal analysis shows no security vendors flagged it as malicious out of 94, highlighting its ability to evade detection.”
Additional impersonating domains like phillips66shop[.]com and phillips66lubricants[.]ru further illustrate the industrial scale of the campaign.
Hunt researchers conclude that attackers are combining phishing with fraud in increasingly industrialized ways. “The content is recycled to scale… while the ‘Chev Corp Stocks’ HYIP template blends brand abuse with investment-fraud pretexts.”
Infrastructure is deliberately scattered across U.S. and European hosting providers, with operators reusing SSL certificates and server blocks to sustain campaigns while avoiding takedowns.
The Hunt Intelligence report underscores a growing trend: phishing against critical infrastructure isn’t just about credentials—it’s about fraud, persistence, and erosion of trust in global brands.
As the researchers warn, “The observed U.S.-focused phishing campaigns function as resilient cloning infrastructures by reusing artifacts, centralizing data exfiltration, and blending credential theft with financial fraud.”
- Kaspersky Report: Energy Industry becomes the largest area affected by vulnerabilities in industrial automation systems
- SpyNote’s New Lure: The Stealthy Campaign Using Fake App Stores
- Critical WordPress Plugin Vulnerability Puts 90,000 Sites at Risk
- Beyond Cryptominers: A New Malware Strain Is Hijacking Exposed Docker APIs