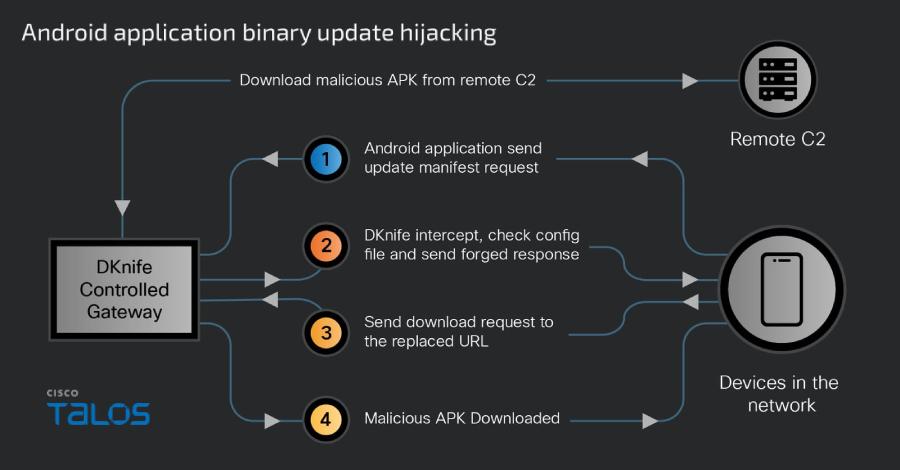
China-Linked DKnife AitM Framework Targets Routers for Traffic Hijacking, Malware Delivery
Cybersecurity researchers have taken the wraps off a gateway-monitoring and adversary-in-the-middle (AitM) framework dubbed DKnife that's operated by Chin…