The cybersecurity landscape demands sophisticated tools to identify and exploit vulnerabilities effectively, with Nessus vs Metasploit representing one of the most powerful combinations in modern penetration testing.
As cyber threats continue to evolve rapidly, security professionals require comprehensive solutions that can both discover security weaknesses and validate their exploitability through controlled testing environments.
The integration of Nessus vulnerability scanner with the Metasploit exploitation framework creates a synergistic approach to vulnerability assessment and penetration testing that has become the industry standard for ethical hackers and security researchers worldwide.
This technical research article explores the comprehensive comparison between Nessus and Metasploit, examining their individual capabilities, integration methodologies, and practical exploitation techniques.
Through detailed analysis of both tools’ strengths, limitations, and real-world applications, security professionals can better understand how to leverage these platforms for maximum effectiveness in their vulnerability assessment and penetration testing operations.
The combination of automated vulnerability discovery with targeted exploitation capabilities provides organizations with the insights needed to strengthen their security posture against advanced persistent threats and sophisticated attack vectors.
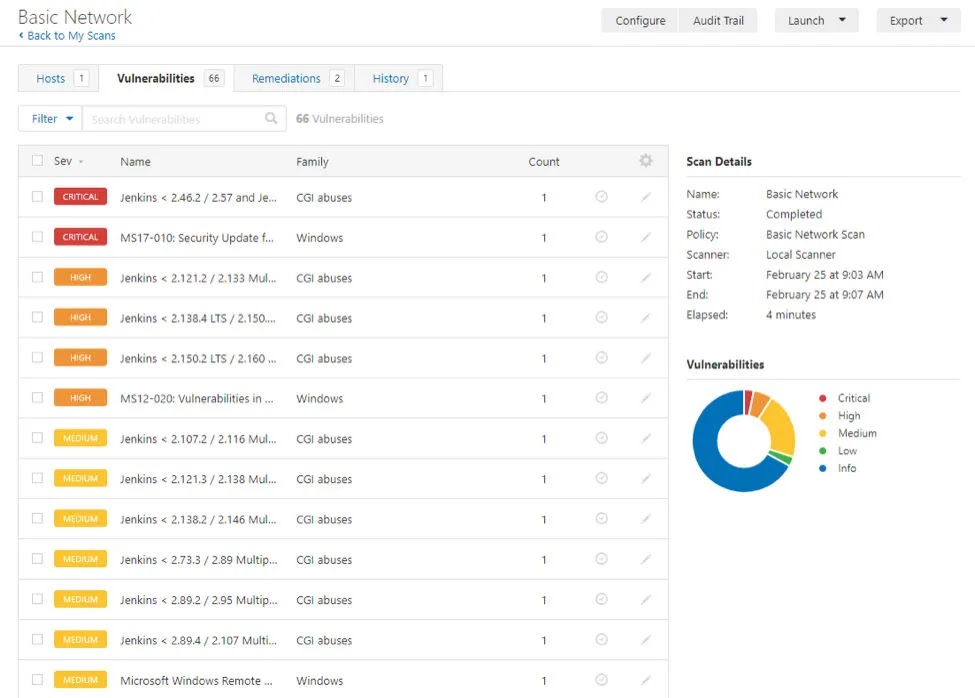
Understanding Nessus
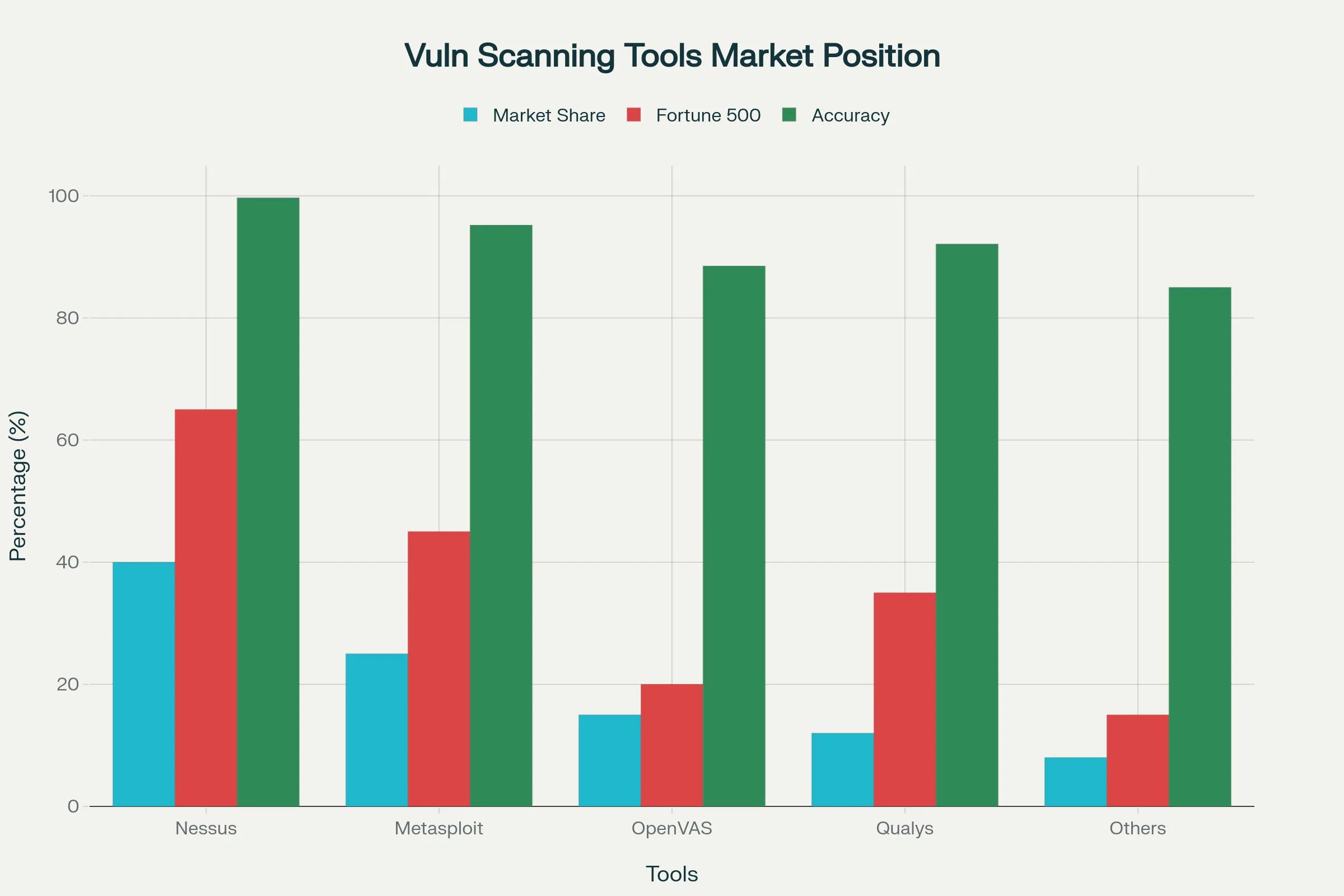
Nessus stands as the world’s most widely deployed vulnerability assessment solution, developed by Tenable Network Security and trusted by over 30,000 organizations globally.
With more than 2 million downloads and adoption by 65% of Fortune 500 companies, Nessus has established itself as the benchmark for vulnerability scanning accuracy and coverage.
The platform features an extensive database of over 140,000 plugins covering more than 50,000 common vulnerability exploits (CVEs), with Tenable releasing more than 100 new plugins weekly to address emerging threats within 24 hours of vulnerability disclosure.
The scanner operates through a sophisticated engine that performs comprehensive network discovery, operating system fingerprinting, and service enumeration across diverse IT environments.
Nessus excels in identifying vulnerabilities across traditional IT assets, web applications, cloud infrastructures, and modern attack surfaces, including IoT devices and containerized environments.
Its credentialed scanning capabilities provide deep visibility into system configurations, missing patches, and security misconfigurations, while unauthenticated scans simulate external attacker perspectives to identify externally exploitable vulnerabilities.
Advanced Scanning Capabilities And Features
The latest Nessus versions include groundbreaking features such as CVSSv4 and EPSS scoring for enhanced vulnerability prioritization, triggered agent scanning in Nessus Manager, and improved offline mode capabilities for air-gapped environments.
These enhancements enable organizations to conduct more precise risk assessments by incorporating real-world threat intelligence and exploit prediction scoring systems.
The platform’s six-sigma accuracy achievement, with a false positive rate of only 0.32 defects per 1 million scans, ensures that security teams can focus their remediation efforts on genuine security threats without wasting resources on non-existent vulnerabilities.
Nessus supports multiple scanning methodologies, including network-based vulnerability assessments, web application security testing, and compliance auditing against frameworks such as PCI DSS, GDPR, and various industry-specific standards.
The platform’s asset discovery capabilities automatically identify and catalog network-connected devices, creating comprehensive inventories that include operating system versions, installed software, open ports, and running services.
This comprehensive visibility enables security teams to maintain accurate attack surface mapping and ensures that no assets remain hidden from security assessments.
Metasploit Framework represents the world’s most sophisticated open-source penetration testing platform, providing security professionals with an extensive arsenal of exploits, payloads, and post-exploitation tools.
Developed by Rapid7 and continuously enhanced by a global community of security researchers, Metasploit contains over 2,180 working exploits targeting vulnerabilities across Windows, Unix/Linux, and macOS systems, along with 592 payload options for diverse attack scenarios.
The framework’s modular architecture enables security professionals to combine any exploit with compatible payloads, creating customized attack vectors tailored to specific target environments and testing objectives.
The platform operates on five primary module types: exploit modules for delivering payloads through vulnerability exploitation, payload modules containing the actual code executed on target systems, auxiliary modules providing non-exploit functionality like scanning and fuzzing, post-exploitation modules for maintaining access and gathering intelligence, and encoder modules for evading security detection systems.
This comprehensive toolkit enables penetration testers to simulate real-world attack scenarios, from initial reconnaissance through complete system compromise and lateral movement across network infrastructures.
Post-Exploitation And Advanced Capabilities
Metasploit’s Meterpreter payload stands as one of the most powerful post-exploitation tools available, providing an interactive shell that operates entirely in memory without writing files to disk.
This advanced payload enables security professionals to perform sophisticated post-exploitation activities, including privilege escalation, credential harvesting, file system manipulation, network pivoting, and persistence establishment.
The framework integrates seamlessly with vulnerability scanners like Nessus, enabling automated correlation between discovered vulnerabilities and available exploits for streamlined penetration testing workflows.
Recent additions to the Metasploit arsenal include Shadow Credentials modules for Active Directory exploitation, critical CVE modules like CVE-2024-3400 for PAN-OS GlobalProtect Gateway exploitation, and enhanced automation capabilities for large-scale security assessments.
The framework’s database integration allows security teams to import vulnerability scan results from multiple sources, creating centralized repositories of attack surface intelligence that can be queried, filtered, and analyzed to prioritize high-impact security testing activities.
The integration of Nessus with Metasploit creates a powerful vulnerability discovery and exploitation pipeline that maximizes the efficiency of security assessments.
This workflow begins with comprehensive Nessus vulnerability scanning to identify potential attack vectors, followed by systematic exploitation using Metasploit’s extensive exploit database to validate the practical impact of discovered vulnerabilities.
The integration process leverages both tools’ strengths: Nessus provides broad vulnerability coverage and accurate asset intelligence, while Metasploit delivers precise exploitation capabilities and post-compromise simulation tools.
Security professionals can establish this integration through multiple methodologies, including direct Nessus API connectivity within the Metasploit console, manual import of Nessus report files in .nbe or .nessus formats, and automated scripting solutions that synchronize vulnerability data between platforms.
The Nessus Bridge plugin enables real-time connectivity between tools, allowing penetration testers to initiate vulnerability scans from within the Metasploit console and automatically import results for immediate exploitation analysis.
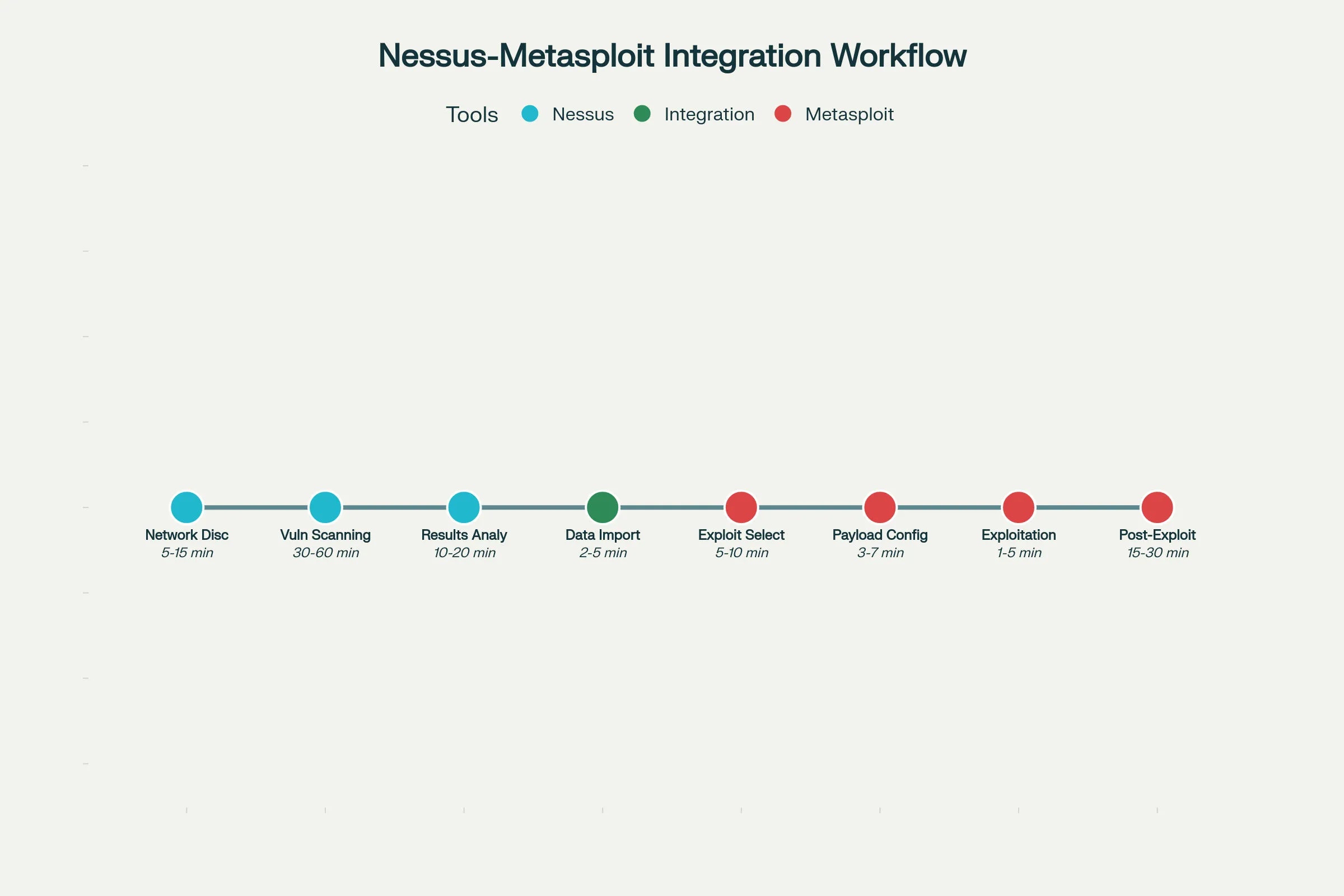
Step-by-Step Integration Process
The practical implementation of Nessus via Metasploit begins with network reconnaissance using Nessus’s asset discovery capabilities to identify active hosts, open ports, and running services across the target environment.
Following initial discovery, comprehensive vulnerability scanning analyzes identified assets for security weaknesses, misconfigurations, and unpatched software vulnerabilities.
The scanner’s credentialed assessment capabilities provide deeper visibility into system configurations, installed software versions, and local security policies that may not be visible through external scanning methodologies.
Once vulnerability scanning completes, security professionals export results in compatible formats and import them into the Metasploit database using the db_import command.
This process populates the framework’s database with comprehensive vulnerability intelligence, including CVE identifiers, affected services, exploit difficulty ratings, and potential impact assessments.
The integrated data enables automated correlation between discovered vulnerabilities and available Metasploit exploit modules, significantly reducing the time required to identify viable attack vectors and exploitation opportunities.
Strengths And Limitations
The Nessus vs Metasploit comparison reveals complementary strengths that make their combination particularly powerful for comprehensive security assessments.
Nessus excels in broad vulnerability discovery, offering unparalleled CVE coverage, high-accuracy scanning, and extensive plugin libraries that identify security weaknesses across diverse technology platforms and configurations.
Its automated scanning capabilities enable rapid assessment of large network environments, while detailed reporting features provide comprehensive documentation for compliance and remediation planning purposes.
Metasploit’s primary strengths lie in exploitation validation and post-compromise simulation, offering security teams the ability to demonstrate real-world attack impacts and business risk exposure.
The framework’s extensive exploit database, advanced payload options, and sophisticated post-exploitation tools enable realistic simulation of advanced persistent threat (APT) scenarios and sophisticated attack campaigns.
However, Metasploit requires significant technical expertise for effective utilization and may not identify vulnerabilities that lack corresponding exploit modules in its database.
Performance And Usability Comparison
From a performance perspective, Nessus demonstrates superior scanning speed and accuracy, with its optimized scan engine capable of assessing thousands of network assets simultaneously while maintaining minimal false positive rates.
The platform’s user-friendly web interface and extensive policy templates enable rapid deployment and configuration, making it accessible to security professionals with varying technical expertise levels.
Nessus’s comprehensive reporting capabilities provide executive-level summaries alongside detailed technical findings, supporting both strategic decision-making and tactical remediation activities.
Metasploit requires more specialized knowledge but provides unmatched flexibility for advanced penetration testing scenarios and security research activities.
The framework’s command-line interface and modular architecture enable experienced security professionals to create custom attack scenarios and develop novel exploitation techniques.
While this complexity may challenge novice users, it provides expert practitioners with the tools needed to simulate sophisticated threat actors and advanced attack methodologies that automated scanners cannot replicate.
Real-World Exploitation Scenarios And Case Studies
Practical application of Nessus via Metasploit methodology demonstrates significant value in real-world penetration testing engagements and security assessments.
Consider a scenario where Nessus identifies an unpatched Windows system vulnerable to MS17-010 (EternalBlue), the infamous vulnerability exploited by WannaCry ransomware.
Security professionals can leverage this intelligence to configure the appropriate Metasploit exploit module (exploit/windows/smb/ms17_010_eternalblue), establish reverse TCP payloads, and demonstrate complete system compromise within minutes of vulnerability discovery.
Advanced exploitation scenarios involve multi-stage attacks where initial Nessus reconnaissance identifies web application vulnerabilities, database misconfigurations, and network service weaknesses across interconnected systems.
Security teams can then orchestrate complex attack chains using Metasploit’s pivoting capabilities, moving laterally through compromised networks while maintaining persistence and avoiding detection.
These realistic attack simulations provide organizations with concrete evidence of potential impact and support strategic security investment decisions.
Market Trends And Future Developments
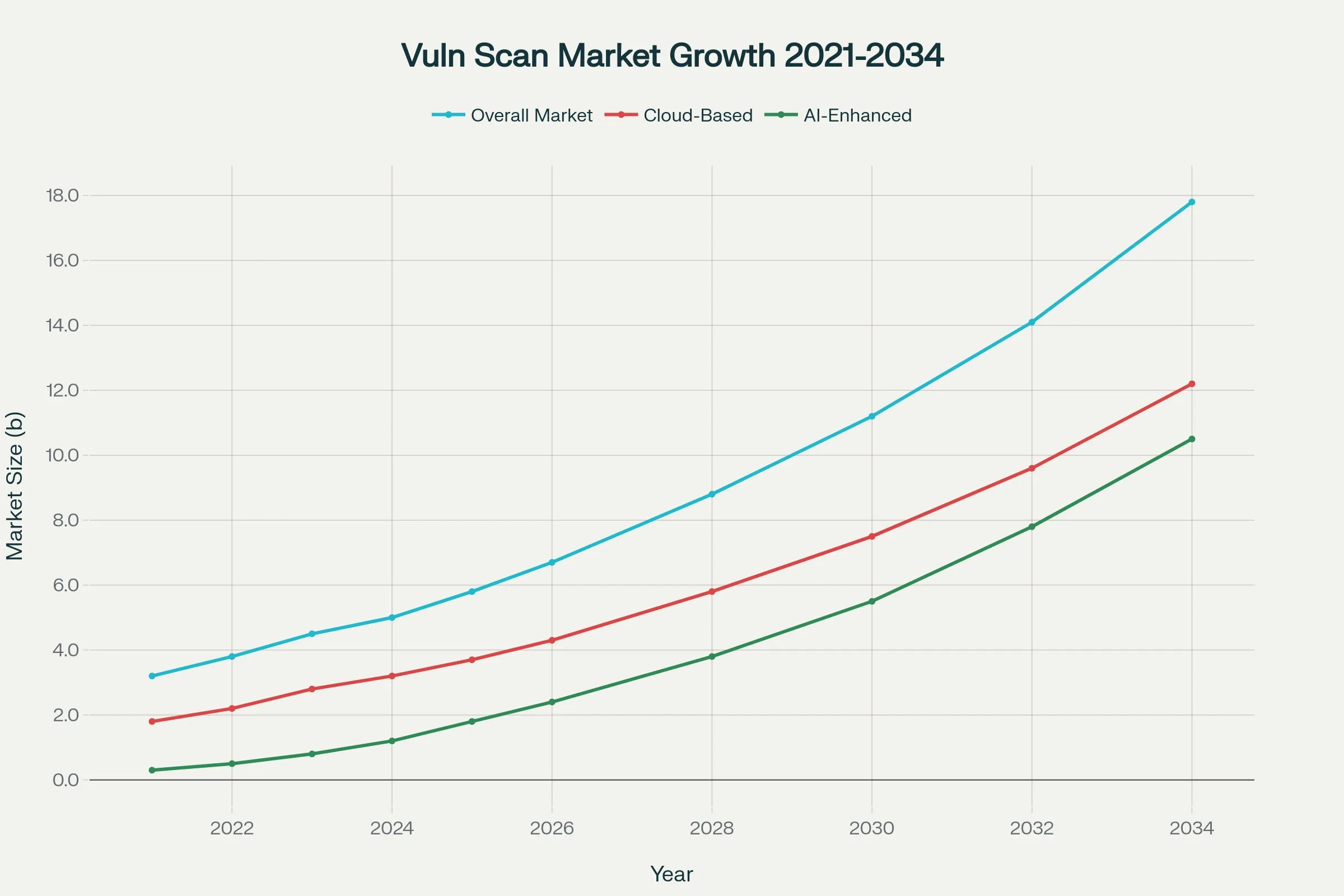
The vulnerability scanning market continues experiencing rapid growth, with global market valuation projected to reach $11 billion by 2032, reflecting a compound annual growth rate of 9% driven by increasing cyber threats and regulatory compliance requirements.
Cloud-based vulnerability scanning solutions represent the fastest-growing segment, with 64% of organizations preferring cloud-native platforms for their scalability, accessibility, and reduced infrastructure requirements.
This shift toward cloud-based security tools aligns with broader digital transformation initiatives and the increasing adoption of DevSecOps practices across industries.
Artificial intelligence integration is revolutionizing vulnerability management capabilities, with AI-enhanced scanning tools projected to reach $10.5 billion by 2034, growing at a CAGR of 14.20%.
These advanced platforms incorporate machine learning algorithms for improved threat detection, automated vulnerability prioritization, and predictive risk assessment capabilities.
The integration of AI technologies enables security teams to process vast amounts of vulnerability data more efficiently while reducing false positive rates and improving remediation prioritization accuracy.
Zero Trust Architecture adoption is driving increased demand for continuous vulnerability assessment and validation capabilities, with organizations requiring real-time security posture monitoring across distributed network environments.
The combination of Nessus vulnerability intelligence with Metasploit exploitation validation supports Zero Trust implementations by providing continuous verification of security controls and assumption validation.
This approach enables organizations to identify security gaps in their Zero Trust implementations before malicious actors can exploit them.
DevSecOps integration represents another significant trend, with security teams incorporating vulnerability scanning and penetration testing tools directly into continuous integration/continuous deployment (CI/CD) pipelines.
This shift-left security approach enables organizations to identify and remediate vulnerabilities during development phases rather than post-deployment, significantly reducing remediation costs and security risk exposure.
The automation capabilities of both Nessus and Metasploit support these integration requirements through API connectivity and scriptable interfaces.
The combination of Nessus vulnerability scanning with Metasploit exploitation capabilities provides security organizations with unparalleled visibility into their security posture and a realistic assessment of potential attack impacts.
This powerful integration enables comprehensive security testing that goes beyond simple vulnerability identification to demonstrate actual exploitability and business risk exposure.
Organizations implementing this methodology gain competitive advantages through improved security awareness, more effective resource allocation, and enhanced regulatory compliance capabilities.
Security professionals should prioritize developing expertise in both platforms while maintaining focus on ethical testing practices and comprehensive documentation of security findings.
The evolving threat landscape requires continuous learning and adaptation, with security teams staying current on emerging vulnerabilities, new exploitation techniques, and advanced defense strategies.
Investment in training and certification programs ensures that security personnel can maximize the value of these sophisticated tools while maintaining professional standards and ethical boundaries.
Modern cybersecurity demands proactive approaches that combine automated discovery with manual validation to address sophisticated threat actors and advanced attack methodologies.
The integration of Nessus and Metasploit represents a mature, proven approach that provides organizations with the intelligence and capabilities needed to maintain robust security postures in increasingly complex digital environments.
As cyber threats continue evolving, this combination will remain essential for comprehensive security assessment and risk management programs across all industry sectors.
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant Updates.




