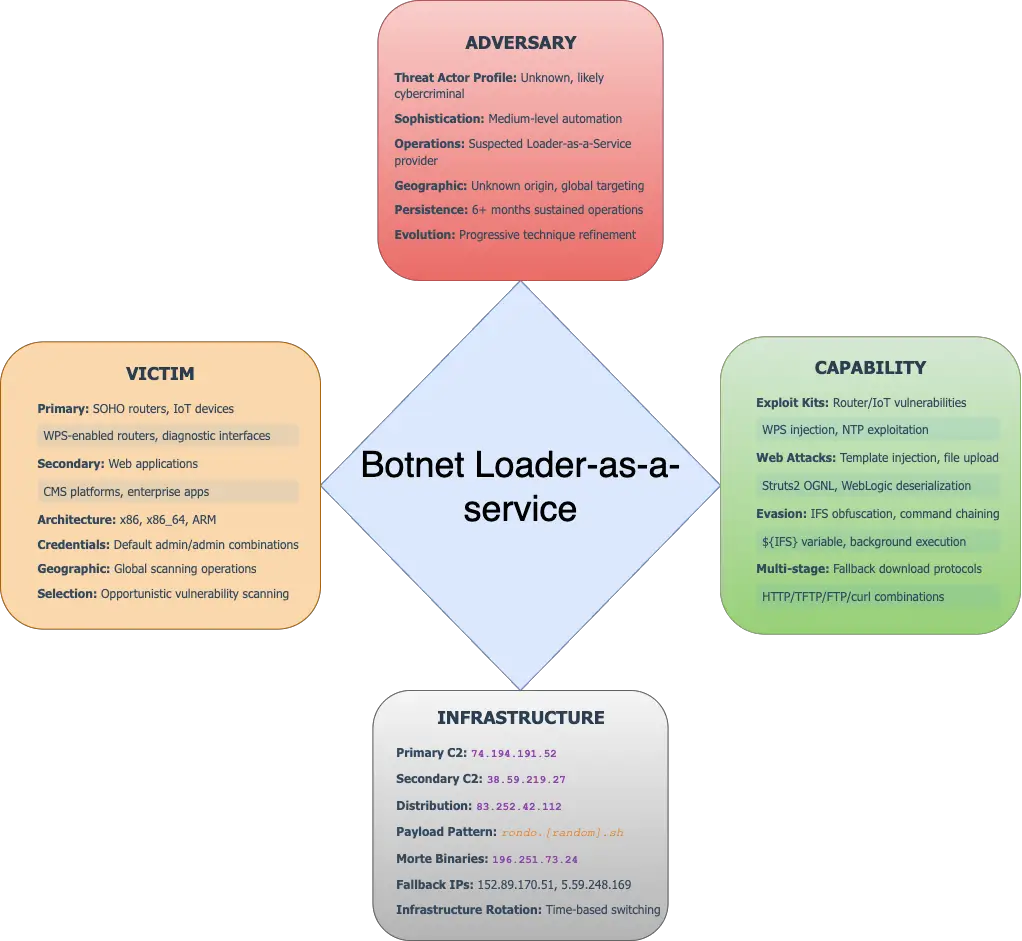
Researchers at CloudSEK Threat Intelligence (TRIAD) have exposed a sophisticated botnet operation that systematically compromises SOHO routers, IoT devices, and enterprise applications through web-based command injection . The campaign, which relies on a Loader-as-a-Service (LaaS) model, has been active for at least six months and shows signs of rapid growth.
CloudSEK observed a major spike in malicious activity this summer: “The operation shows a 230% attack spike from July-August 2025, deploying multi-architecture malware including Morte binaries and cryptomining payloads.”
The discovery was made possible after CloudSEK analysts accessed exposed command-and-control (C2) logs, revealing detailed insights into the attackers’ infrastructure and techniques.
The botnet relies heavily on command injection via web interfaces, abusing poorly sanitized POST parameters such as ntp, syslog, and hostname fields. As CloudSEK explains, “Attacker injects shell commands into unsanitized POST parameters (e.g., ntp, remote_syslog, hostname, ping) so the device executes wget/curl | sh.”
Key techniques include:
- Exploiting default credentials (admin:admin) through brute force or credential sprays.
- Targeting firmware upgrade and diagnostics endpoints to run arbitrary code.
- Leveraging BusyBox tools for multi-platform payload delivery.
- Rotating infrastructure across dozens of IPs to evade takedowns.
- The campaign also exploits known CVEs, such as CVE-2019-16759 (vBulletin pre-auth RCE), CVE-2019-17574 (WordPress Popup Maker plugin), and CVE-2012-1823 (PHP-CGI RCE).
Once devices are compromised, attackers use a staged delivery approach:
- Small shell scripts act as droppers.
- Native binaries like morte.x86 and morte.x86_64 are installed for persistence.
- Cryptomining payloads are deployed, hijacking resources for profit.
CloudSEK notes, “Payloads that connect to mining pools or use JSON-RPC getwork/eth_getWork suggest mining as monetization.”
Beyond cryptojacking, the botnet also supports HTTP-based C2 polling, enabling operators to issue commands, collect reconnaissance, and decide whether to retain access for further use or resale.
The operation spans both consumer and enterprise ecosystems:
- SOHO routers and embedded Linux devices.
- Enterprise apps, notably Oracle WebLogic, WordPress, and vBulletin servers.
- Firmware and router diagnostics pages like wlwps.htm, wan_dyna.html, and login.shtml.
Devices compromised in this way can be repurposed for DDoS campaigns, mining, or resale on underground markets.
CloudSEK warns that the campaign is still evolving: “We can ascertain with high confidence that the threat actors will continue rapid exploitation and will considerably expand the list of targeted devices in the next 6 months.”
Given the Loader-as-a-Service model, the infrastructure could be weaponized by multiple criminal groups, accelerating its growth and persistence across the global threat landscape.
- A Massive Coordinated Attack Is Probing Cisco ASA Devices
- Hacker announced to break the Nintendo’s Switch firmware, it will be released this summer
- Firefox’s New AI Feature Is Causing Major CPU Spikes and Draining Batteries
- A Storm Is Coming: A Massive Coordinated Attack Is Probing RDP Connections
- SPIKEDWINE’s Espionage Campaign with WINELOADER Backdoor Revealed