In June 2025, a new ransomware group known as Kawa4096 surfaced, launching disruptive attacks against multinational organizations in finance, education, and services. Victims have been reported in both Japan and the United States, underscoring the group’s global reach.
According to AhnLab, “Kawa4096 is quickly gaining attention for its rapid and widespread activity… They maintain a data leak site on the Tor network, where they publicly disclose information about their victims.”
Kawa4096 employs the now-standard double extortion tactic: stealing data before encrypting files. Victims are directed to a dedicated claim URL on the group’s leak site, where sensitive information may be publicly exposed if ransom demands are not met.
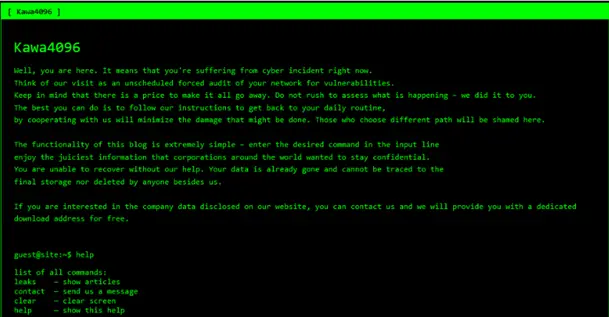
The report notes, “Evidence suggests they use a double extortion tactic—exfiltrating data before encrypting it during an attack.”
Interestingly, the design of their leak site resembles that of the Akira ransomware group, which is known for its retro 1980s command-line style. AhnLab highlights that this may not be coincidence: “New ransomware groups often adopt branding elements from notorious predecessors to amplify psychological pressure—instilling fear and perceived credibility in victims.”
A distinct feature of Kawa4096 is its command-line execution behavior. If launched without arguments, it automatically re-runs itself with the -all option, initiating global encryption.
Encryption behaviors include:
- -d=<directory> → encrypt a specified directory.
- -all → encrypt all targeted files.
- -dump → invoke MiniDumpWriteDump to generate a crash dump file in the local directory.
To prevent multiple executions, the ransomware creates a mutex named SAY_HI_2025 using the CreateMutexA API. If the mutex already exists, the program terminates.
Kawa4096’s configuration is embedded in its resource section, dictating exclusions and behaviors. Notably:
File extension exclusions include .exe, .sys, .dll, and .lnk, ensuring systems remain bootable.
Directory exclusions skip core OS paths like Program Files and PerfLogs.
File exclusions cover boot.ini, desktop.ini, and other startup-critical files.
Before encryption, processes such as sqlservr.exe, excel.exe, and outlook.exe are terminated to free files for encryption.
The ransomware applies partial encryption for efficiency. AhnLab explains, “It divides a file into 64 KB chunks and encrypts only 25% of the chunks… encrypting large files in full can be time-consuming, so by encrypting only parts, the ransomware aims to maximize the number of files it can affect within a short time.”
Kawa4096 uses the Salsa20 stream cipher, appending encrypted files with a random 9-character alphanumeric extension.
Each infected system receives a ransom note titled !!Restore-My-file-Kavva.txt, created in both encrypted directories and the root directory. AhnLab points out, “The ransom note used by Kawa4096 shows a high degree of similarity to that of the Qilin ransomware. Both the content and format are nearly identical.”
The note informs victims of stolen data, threatens public leaks, and provides negotiation contact details including a Tor site and QTOX ID.
To ensure victims cannot restore files, the ransomware executes commands to delete all Volume Shadow Copies using:
- vssadmin.exe Delete Shadows /all /quiet
- wmic shadowcopy delete /nointerface
AhnLab concludes, “It is presumed that the threat actor intended to completely disable the victim’s backup recovery means to prevent them from attempting to recover their data.”
- Hackers Exploit Google Ads to Spread Malware Disguised as Popular Software
- Water Sigbin Threat Actor Targets Oracle WebLogic Servers to Deploy XMRig Cryptominer
- NightshadeC2: A New Botnet Is Using “UAC Prompt Bombing” to Bypass Windows Defender
- Let’s Encrypt Root gains the trust of all major root programs



