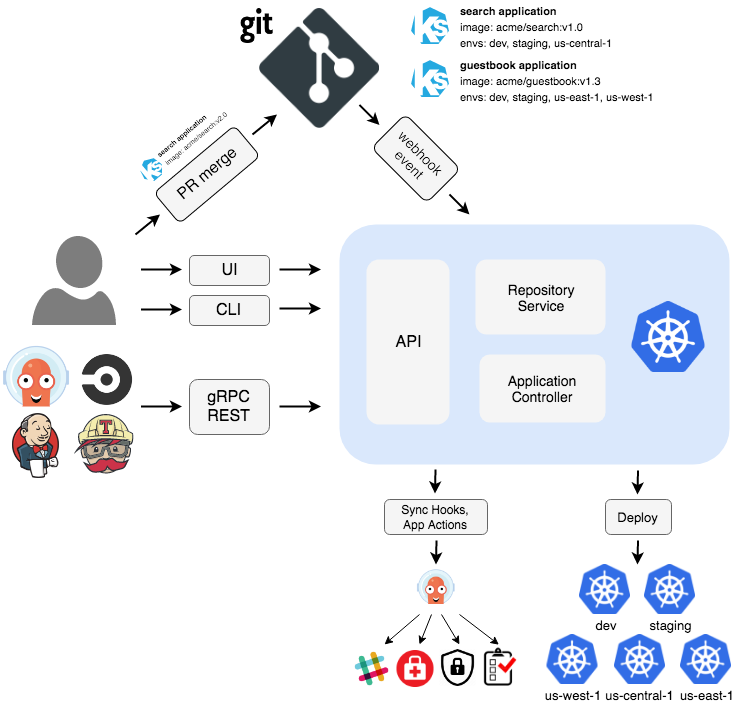
The Argo CD project has released patches addressing several denial-of-service (DoS) that could allow attackers to crash the argocd-server process with a single unauthenticated HTTP request. The affect webhook integrations with Azure DevOps, Bitbucket Server, and Gogs, as well as a race condition in repository credential handling.
One of the most severe issues, CVE-2025-59538, carries a CVSS score of 7.5. The advisory explains: “In the default configuration, webhook.azuredevops.username and webhook.azuredevops.password [are] not set, Argo CD’s /api/webhook endpoint crashes the entire argocd-server process when it receives an Azure DevOps Push event whose JSON array resource.refUpdates is empty.”
Because the handler does not check the array length, an attacker can send a crafted webhook event with “refUpdates”: [], causing an index-out-of-range panic. “A single unauthenticated HTTP POST is enough to kill the process.”
A similar issue exists with Bitbucket Server webhooks. Tracked as CVE-2025-59531 (CVSS 7.5), it occurs when the JSON field repository.links.clone is anything other than an array. The unsafe type assertion causes the server to panic and restart.
As the advisory warns, “A single unauthenticated curl request can push the control-plane into CrashLoopBackOff; repeating the request on each replica causes a complete outage of the API.”
The third webhook-related , CVE-2025-59537 (CVSS 7.5), affects Gogs integrations. “Argo CD’s /api/webhook endpoint will crash the entire argocd-server process when it receives a Gogs push event whose JSON field commits[].repo is not set or is null.”
The lack of input validation allows attackers to send malformed JSON and repeatedly crash the service.
Beyond webhook handling, a race condition identified as CVE-2025-55191 (CVSS 6.5) impacts Argo CD’s repository credentials handler. “Concurrent repository credential operations (create/update/delete) accessing the same map … without mutex protection for map access” can cause the server to panic with a concurrent map read and map write error.
While this issue requires a valid API token with repository permissions, it can still disrupt GitOps workflows by repeatedly forcing the server into a denial-of-service state.
The Argo CD team has issued fixes for all in the following versions:
- 2.14.20
- 3.2.0-rc2
- 3.1.8
- 3.0.19
Administrators are strongly urged to upgrade immediately. In the meantime, the project recommends configuring webhook secrets to restrict access: “If you do not use Azure DevOps, Bitbucket Server, or Gogs, you can set the webhook secrets to long, random values to effectively disable webhook handling for those payloads.”
- Argo CD Alert: XSS Flaw (CVSS 9.1) Allows Kubernetes Hijacking
- CVE-2025-23171 & CVE-2025-23172: Versa Director Bugs Open Doors to Webshell Uploads and Command Execution
- Unpatched Gogs Vulnerabilities: A Ticking Time Bomb for Source Code
- Behind the Commit: CVSS 10.0 Bug Lets Attackers Hijack Gogs Servers