A newly disclosed in Notepad++ v8.8.3 has been assigned CVE-2025-56383. The , rated CVSS 6.5, allows attackers to hijack Notepad++’s DLL loading process, potentially enabling the execution of arbitrary malicious code.
According to the disclosure, “Notepad++ v8.8.3 has a DLL hijacking , which can replace the original DLL file to execute malicious code.”
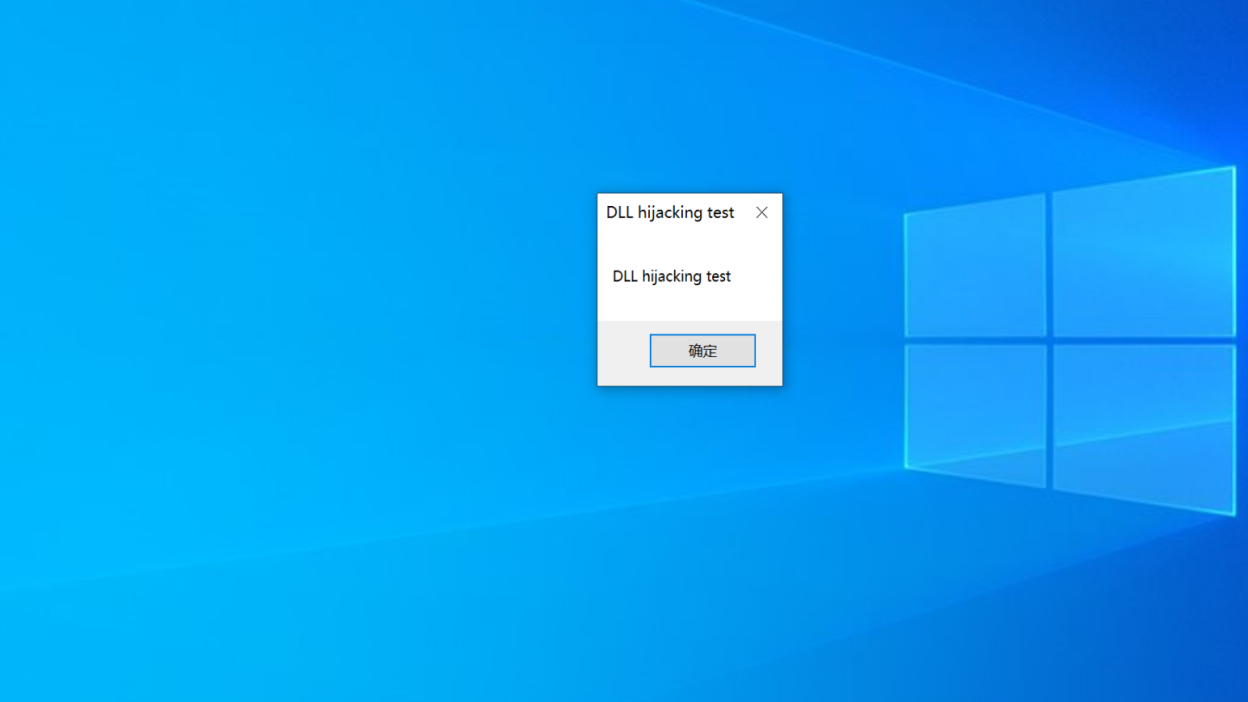
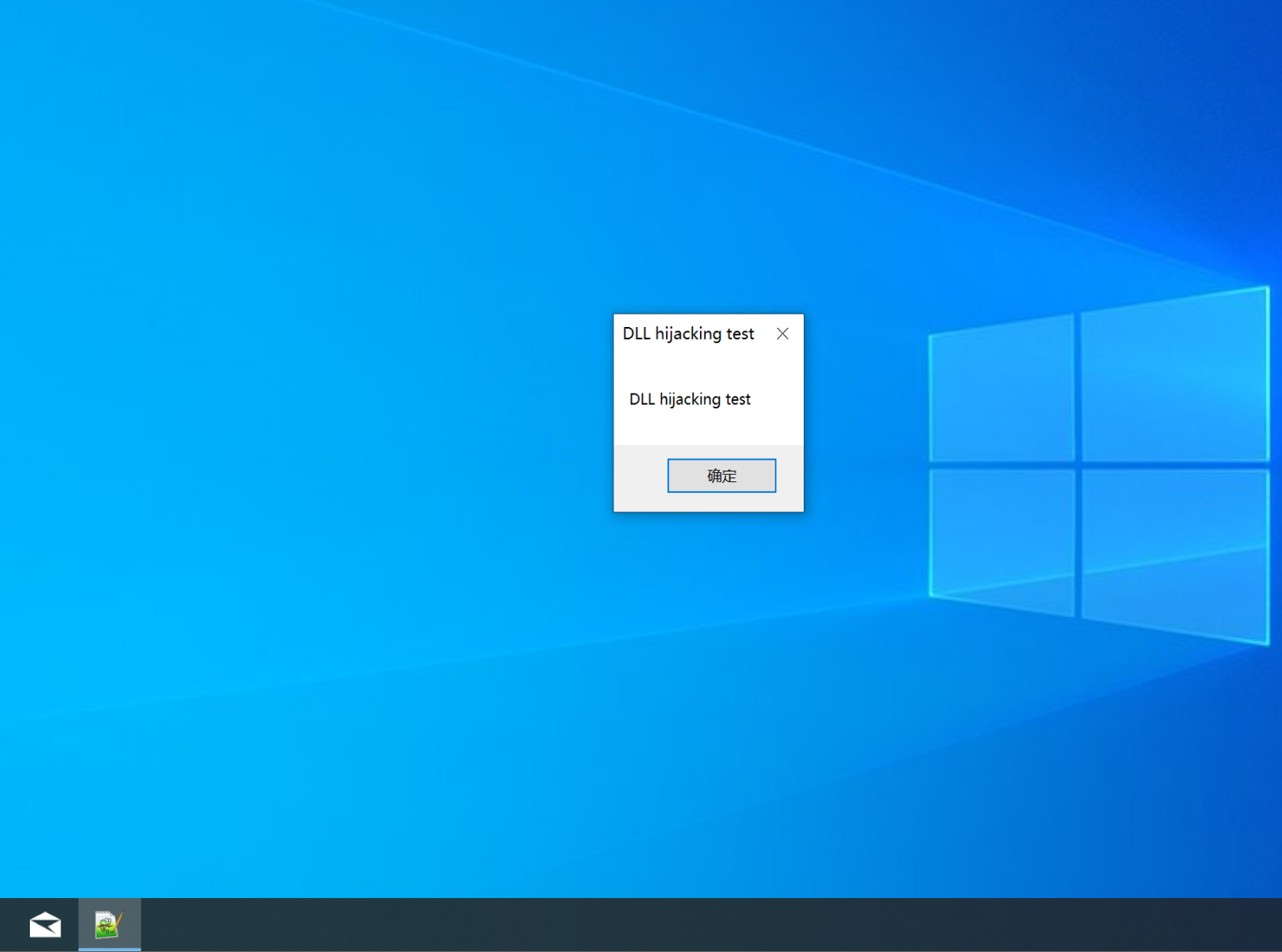
The attack exploits the fact that Notepad++ automatically loads certain DLLs during execution. By replacing a trusted DLL (e.g., NppExport.dll) with a malicious one, attackers can ensure their code runs whenever the program is launched.
The advisory explains: “Replace the original DLL (such as Notepad++pluginsNppExportNppExport.dll) with a DLL file with the same name containing malicious code (the original export function is forwarded to the original DLL), so that when executing notepad++.exe, malicious code can be executed.”
This DLL hijack is confirmed to work when starting Notepad++, effectively giving attackers persistence and execution on the victim’s machine.
A working proof-of-concept (PoC) has been released on GitHub, complete with demonstration images of the attack chain. The PoC shows how the forged NppExport.dll executes malicious code while forwarding calls to the original original-NppExport.dll, maintaining functionality but compromising .
While this vulnerability requires local access or the ability to drop malicious DLLs in the Notepad++ installation path, it significantly increases the risk of privilege escalation and malware persistence. Attackers could leverage this as part of a supply chain attack, trojanized installer, or insider threat scenario.
Given Notepad++’s popularity among developers, administrators, and professionals, the attack surface is broad.
- Notepad Goes Private: Microsoft Adds On-Device AI
- Popular Chinese Text Editors Compromised in Targeted Attack
- AI Notepad: Rewrite Your Text, Windows 11 Gets Smarter
- PoC Released for Notepad++ Flaw Enables Privilege Escalation to NT AUTHORITYSYSTEM
- Popular Text Editor Notepad++ Compromised in “WikiLoader” Malware Attack