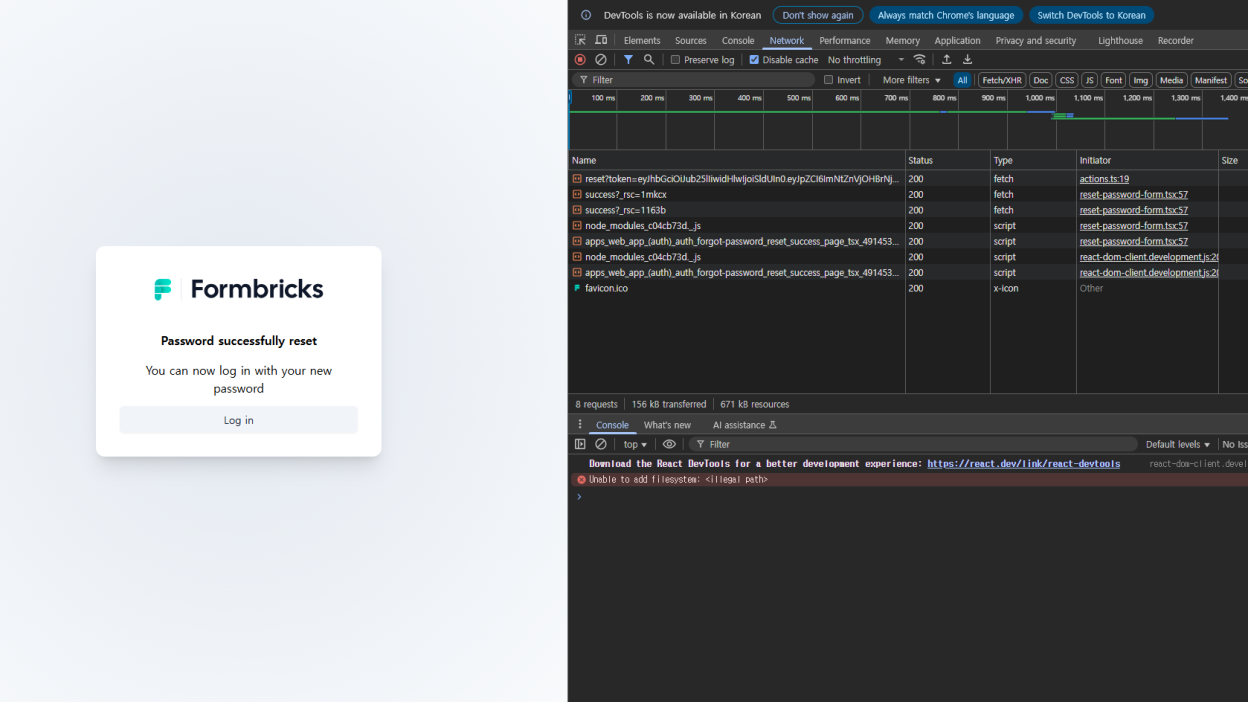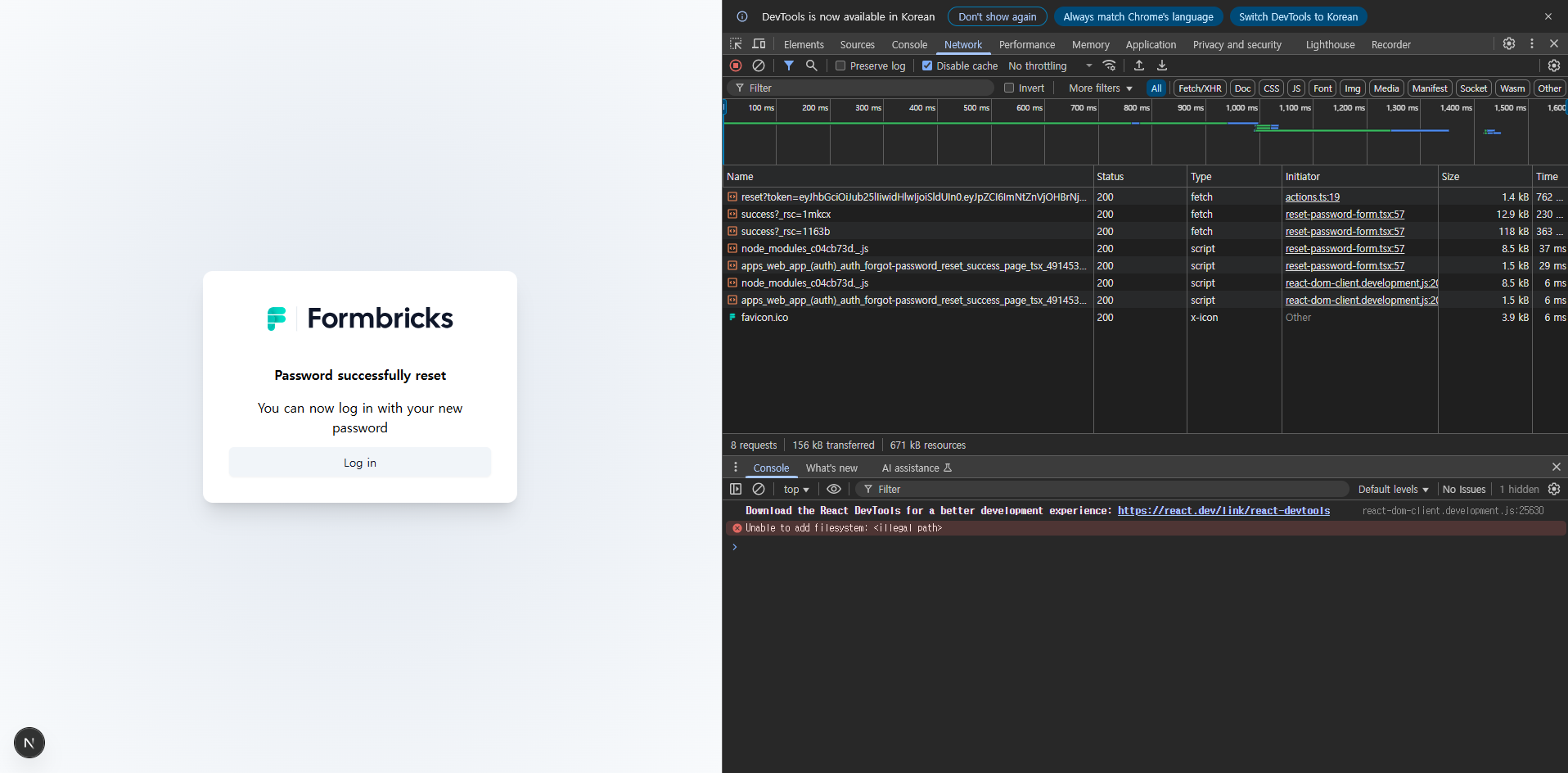
The Formbricks project, an open-source platform for building in-app and website surveys, has released an urgent patch addressing a critical authentication . Tracked as CVE-2025-59934 with a CVSS score of 9.4 (Critical), the allows attackers to bypass JSON Web Token (JWT) verification and reset user passwords without authorization.
The issue stems from improper token validation logic. According to the advisory, “This stems from a token validation routine that only decodes JWTs (jwt.decode) without verifying their signatures. Both the email verification token login path and the password reset server action use the same validator, which does not check the token’s signature, expiration, issuer, or audience.”
An attacker who learns a victim’s user.id could craft a malicious JWT with an alg: “none” header and authenticate as the victim or reset their password.
The advisory explains: “If an attacker learns the victim’s actual user.id, they can craft an arbitrary JWT with an alg: ‘none’ header and use it to authenticate and reset the victim’s password.”
The report provides a working proof-of-concept (PoC):
- Leak the victim’s user.id (e.g., cmfuc8pk60000vxfjud7bcl2w).
- Forge a JWT with {“id”:”<victim_user.id>”} and header alg:”none”.
- Submit it via /auth/forgot-password/reset?token=<forged_JWT>.
- The server accepts the token, queries the database for the user, and resets the password.
As the advisory notes, “verifyToken parses the payload using jwt.decode instead of jwt.verify (no signature or expiry checks).”
This vulnerability enables full account takeover if the attacker obtains a user’s ID string. Because Formbricks exposed both the email verification and password reset flows to this weakness, an attacker could effectively lock users out of their accounts by resetting credentials at will.
The advisory warns: “Knowing the victim’s actual user.id is enough to arbitrarily change their password.”
Formbricks users should immediately upgrade to version 4.0.1 or later. Until patching is complete, organizations should:
- Restrict access to password reset endpoints.
- Monitor for unusual password reset requests.
- Rotate user credentials if compromise is suspected.
- Hacker forged Windows 11 upgrade website to trick users to download the virus
- Account Takeover Vulnerability Found in Better Auth Library
- UK Forges Strategic AI Alliance with OpenAI to Boost Infrastructure and Safety Research
- Researcher releases a PoC for PHP RCE vulnerability
- CISA Warns of Credential Risks Tied to Oracle Cloud Breach