The Termix project has disclosed a critical authentication bypass in its official Docker image, exposing sensitive SSH configuration data without requiring user login. Tracked as CVE-2025-59951, the carries a CVSS v4 score of 9.2, placing it in the “critical” severity range.
Termix is an open-source, forever-free, self-hosted all-in-one server management platform, offering SSH terminal access, tunneling, remote file management, and more. Termix provides a web-based solution for managing your servers and infrastructure through a single, intuitive interface.
But in affected Docker deployments, that centralization comes with a major risk.
The stems from the way Termix’s backend interprets client IP addresses when running behind an Nginx reverse proxy.
The advisory explains: “The official Docker image provided by Termix, due to being configured with an Nginx reverse proxy, causes the backend to retrieve the proxy’s IP instead of the client’s IP when using the req.ip method. This results in isLocalhost always returning True.”
As a result, the /ssh/db/host/internal endpoint—meant to be restricted—becomes accessible without authentication. Attackers who reach this endpoint can retrieve stored SSH host information, including addresses, usernames, and passwords.
The report emphasizes the severity: “Consequently, the /ssh/db/host/internal endpoint can be accessed directly without login or authentication … posing an extremely high risk.”
The vulnerability is easily reproducible, both in lab and real-world conditions. The advisory notes: “Vulnerable environments can be identified through network asset mapping platforms, and the vulnerability can be stably reproduced.”
One researcher confirmed: “My Termix service is deployed inside a virtual machine, and the host machine can directly access this interface without logging in.”
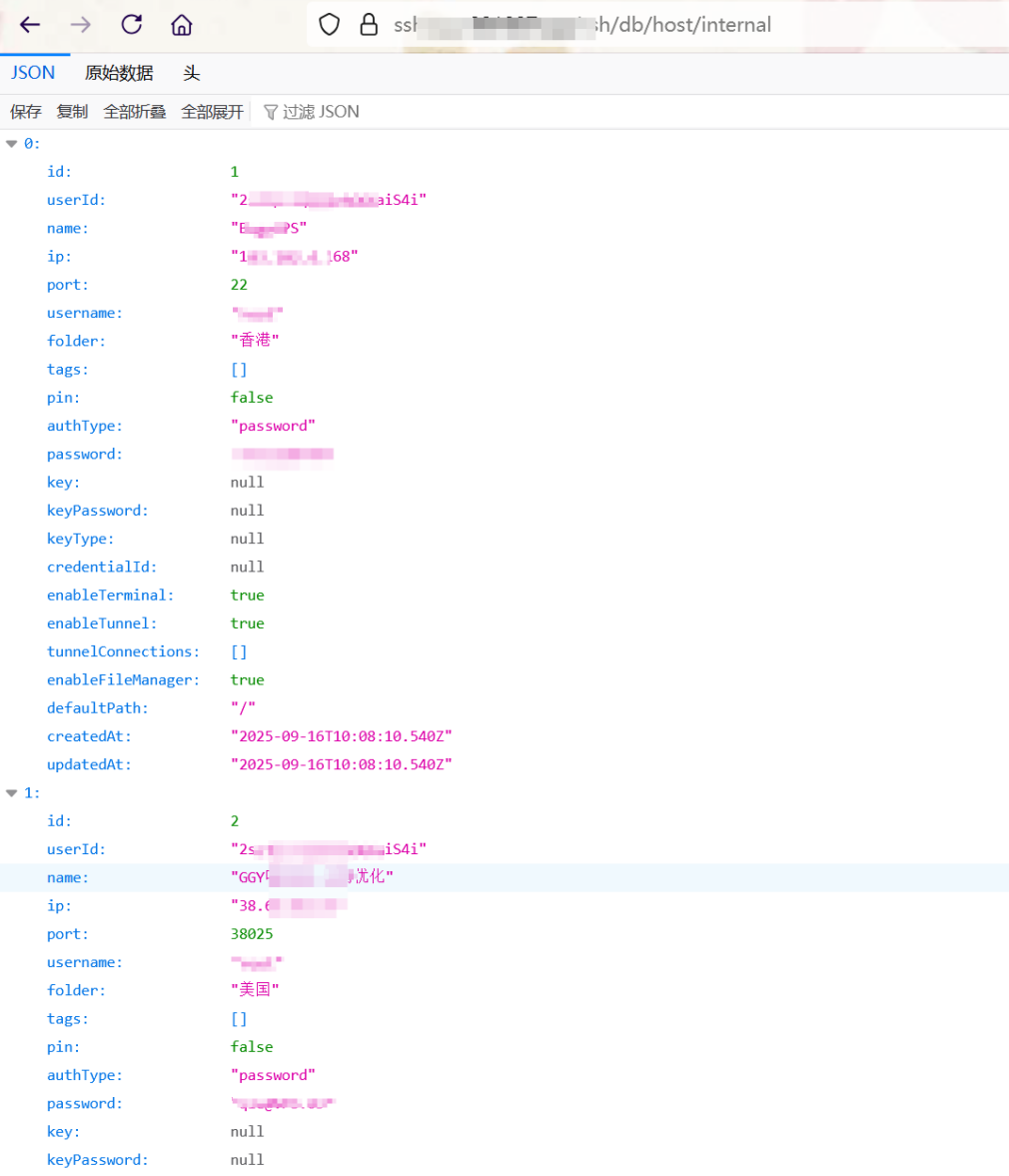
This means any exposed Termix Docker instance could be compromised remotely, with attackers harvesting credentials to pivot deeper into enterprise or personal networks.
A proof-of-concept exploit demonstrates how trivial it is to access the endpoint:
GET /ssh/db/host/internal HTTP/1.1
Host: 192.168.31.163:8080
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:141.0) Gecko/20100101 Firefox/141.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Sec-GPC: 1
Connection: close
Upgrade-Insecure-Requests: 1
If-None-Match: W/"1ab-zbQqwLq8yRYGshOfYUtU/I0BLkQ"
Priority: u=0, iSuch a request returns SSH host details without any form of authentication.
According to the Termix advisory: “Users who use the official Termix docker image, build their own image using the official dockerfile, or utilize reverse proxy functionality will be affected by this vulnerability.”
- Affected versions: release-0.1.1-tag through release-1.6.0-tag
- Patched version: release-1.7.0-tag
The recommended fix is to upgrade immediately to release-1.7.0-tag. Additionally, administrators should modify backend logic to validate against the X-Real-IP header instead of relying solely on req.ip or X-Forwarded-For.



