Ddos
August 30, 2025
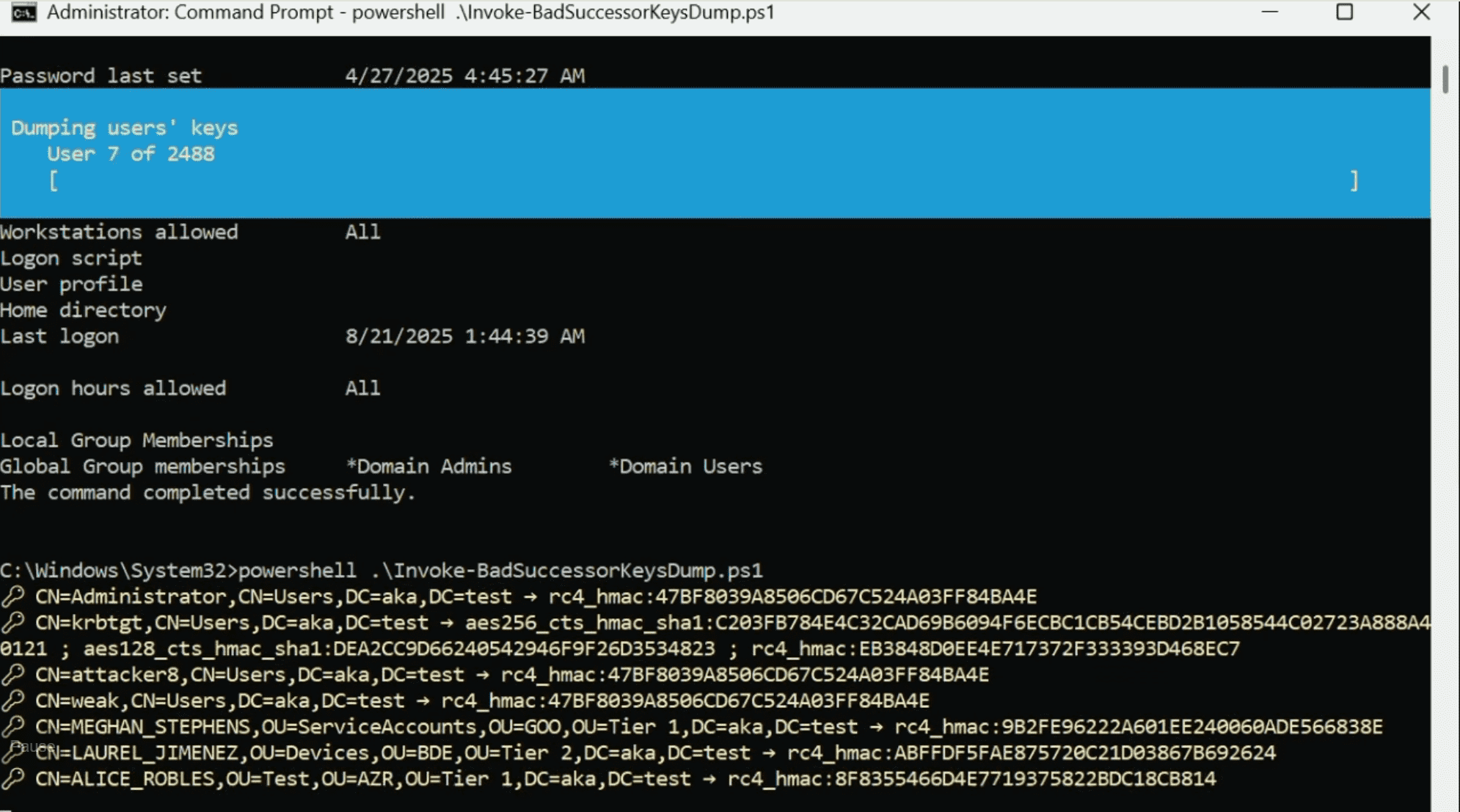
At DEF CON 2025, Akamai security researcher Yuval Gordon revealed the story of BadSuccessor (CVE-2025-53779), an Active Directory (AD) vulnerability in Windows Server 2025’s delegated Managed Service Account (dMSA) feature. The flaw allowed a low-privileged user to escalate directly to Domain Admin, creating one of the most dangerous privilege escalation paths seen in recent years.
Before Microsoft’s patch, the attack abused how AD handled dMSA objects. As Akamai explains: “BadSuccessor abused dMSA — a Windows Server 2025 account type meant to simplify service account management. When a controlled dMSA was linked to any account in AD, the Key Distribution Center (KDC) treated the dMSA as the successor during authentication.”
This effectively merged privileges and handed over Kerberos keys without requiring group changes or special tools. Critically, “control over any Organizational Unit (OU) was enough. An attacker could create a dMSA there and link it to any target — even domain controllers, Domain Admins, Protected Users, or accounts marked ‘sensitive and cannot be delegated’ — and immediately compromise them.”
Less than a week after disclosure, Microsoft assigned CVE-2025-53779 and released a patch. Akamai researchers tested the fix: “After installing the patch, we tried the obvious test: As a user who controls a dMSA, I wrote the link attribute exactly as before. The write still succeeded… but when I authenticated as the dMSA to inherit the target’s privileges and keys, the KDC refused to issue a ticket.”
Instead of blocking the attribute, Microsoft hardened kdcsvc.dll, forcing the KDC to validate that a true mutual pairing exists. Now, “the only way to obtain a valid ticket… was to make the link mutual: The target must also reference the dMSA, mirroring what a real migration produces.”
In short, the direct escalation path was closed.
Despite the patch, Akamai stresses that the underlying technique persists: “Although the vulnerability can be patched, BadSuccessor still lives on as a technique… it didn’t introduce any protection to the link attribute, an attacker can still inherit another account by linking a controlled dMSA and a target account.”
Two exploitation “primitives” remain:
- Credential and Privilege Acquisition – Attackers controlling a dMSA and a target principal can pair them to obtain the target’s keys, acting with its privileges while shifting detection telemetry.
- Targeted Credentials Dump in Compromised Domains – In already-owned environments, BadSuccessor enables secret dumping without relying on DCSync, providing a stealthier alternative.
Akamai recommends a combination of patching and monitoring:
- Patch immediately: Apply Microsoft’s fixes for CVE-2025-53779.
- Audit dMSA creation and link changes: “Audit the creation of dMSAs and changes to the migration link attributes on both sides.”
- Watch for behavioral tells: Repeated dMSA password fetches, enabled accounts linked to dMSAs, or disabled accounts suddenly paired with new dMSAs.
- Tighten delegations: Limit who can create or modify dMSAs to Tier 0 admins.
Related Posts:
- Windows Server 2025 “BadSuccessor” Flaw Allows Domain Takeover (PoC Available, No Patch)
- Microsoft’s August Patch Tuesday: Zero-Day Kerberos Flaw Threatens Domain Admins
- North Korean Hackers Exploit Old Office Flaw to Deploy Keylogger
- Akamai Unveils New VPN Post-Exploitation Techniques: Major Vulnerabilities Discovered in Ivanti and FortiGate VPNs