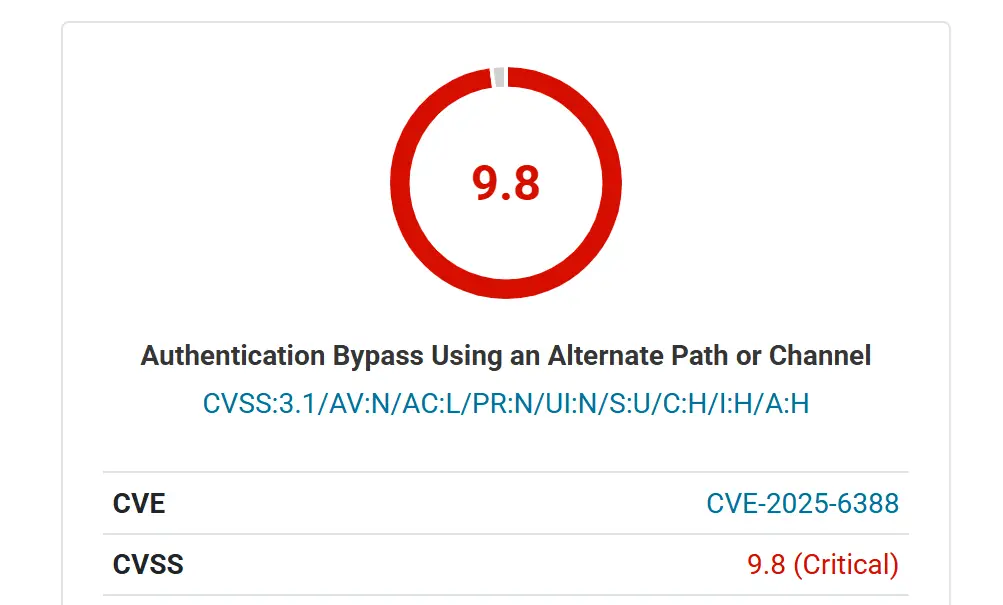
A newly disclosed in the Spirit Framework plugin for WordPress has put thousands of websites at immediate risk of compromise. Tracked as CVE-2025-6388, the carries a CVSS score of 9.8 (Critical) and could allow attackers to bypass authentication, seize control of accounts, and escalate privileges to site administrators.
The affects all versions up to and including 1.2.14 of the Spirit Framework plugin. At its core, the issue lies in improper identity validation within the custom_actions() function.
According to the disclosure, “The Spirit Framework plugin for WordPress is vulnerable to authentication bypass … due to the custom_actions() function not properly validating a user’s identity prior to authenticating them to the site.”
In practice, this means that an attacker who knows the username of a valid account—such as an administrator—can log in without needing the corresponding password.
provider Wordfence confirmed active exploitation, reporting: “Wordfence blocked 20 attacks targeting this vulnerability in the past 24 hours.”

Once inside, adversaries could take over accounts, escalate privileges to administrator, install backdoors, or inject malicious content—all without triggering standard authentication checks.
This type of vulnerability is especially dangerous for WordPress, given its widespread use in powering enterprise, e-commerce, and personal websites worldwide.
The developers have released Spirit Framework version 1.2.15, which includes a patch to properly validate user identities before granting authentication. Website administrators are urged to update immediately.
Failure to patch leaves sites vulnerable to full account takeover, potentially resulting in defacement, data theft, or deployment of malware.