Cybercriminals are abusing AI platforms to create and host fake CAPTCHA pages to enhance phishing campaigns, according to new Trend Micro research.
Attackers are exploiting the ease of deployment, free hosting and credible branding offered by such platforms to set up such pages at speed and scale.
The fake CAPTCHA pages redirect victims to malicious websites hosted by the attackers. This approach makes phishing attacks more likely to succeed as the apparent routine security check makes the malicious link appear more legitimate to the victim and help bypass security tools.
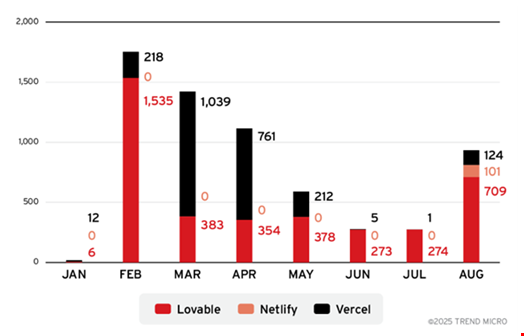
The use of AI platforms for such pages has been observed since January 2025, escalating sharply from February to April, according to Trend Micro data.
The researchers highlighted attackers’ use of three AI-powered platforms – Lovable, which allows anyone to build and host applications with little to no coding knowledge, and Netlify and Vercel, which are AI-native development platforms.
Vercel was linked to 52 phishing emails, Lovable 43 and Netlify three.
The researchers noted that these AI tools allow attackers to set up convincing fake CAPTCHA sites with minimal technical skills.
“On Lovable, attackers can use vibe coding to generate a fake CAPTCHA or phishing page, while Netlify and Vercel make it simple to integrate AI coding assistants in the continuous integration/continuous delivery (CI/CD) pipeline to churn out fake CAPTCHA pages,” the researchers explained.
Additionally, the availability of free tiers on these platforms lowers the cost of entry for launching these sophisticated phishing operations.
“The rise of fake CAPTCHA phishing highlights how attackers are weaponizing AI-powered website creation platforms. While these services drive innovation for legitimate developers, they can also provide cybercriminals with the tools to launch phishing attacks at scale, quickly and at minimal cost,” the Trend Micro researchers wrote in a blog published on September 19.
How the Phishing Campaigns Work
The phishing campaigns typically begin with spam emails carrying urgent messages such as “Password Reset Required” or “USPS Change of Address Notification”.
Clicking the embedded URL directs the target to an apparent CAPTCHA verification page – this serves the dual purpose of making the link appear more legitimate and helping bypass detection tools as automated scanners crawling the page encounter only a CAPTCHA.
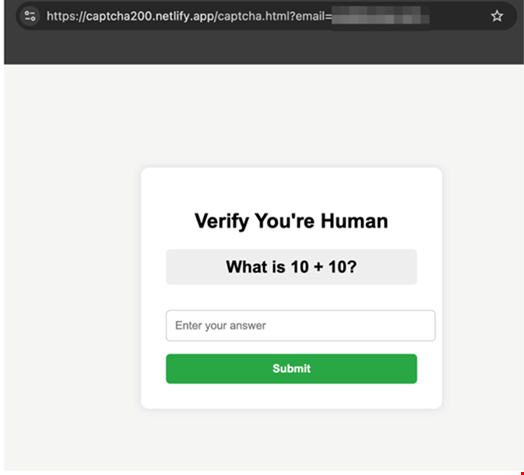
Once the CAPTCHA is completed, the victim is redirected to the actual phishing page, where their credentials and other sensitive data can be stolen.
Trend Micro provided a number of recommendations for organizations on how to mitigate the risks of captcha-based phishing campaigns:
- Educate employees on how to spot captcha-based phishing attempts, including verifying URLs before interacting with captchas
- Implement defenses capable of analyzing redirect chains
- Monitor trusted domains for signs of abuse by tracking traffic to their subdomains



