ACR Stealer represents one of the most sophisticated information-stealing malware families actively circulating in 2025, distinguished by its advanced evasion techniques and comprehensive data harvesting capabilities.
Originally emerging in March 2024 as a Malware-as-a-Service (MaaS) offering on Russian-speaking cybercrime forums, ACR Stealer has rapidly evolved from its predecessor, GrMsk Stealer, into a formidable threat that employs cutting-edge obfuscation methods to bypass modern security solutions.
This malware has gained particular notoriety for its innovative use of legitimate platforms as command-and-control infrastructure, making detection and mitigation exceptionally challenging for security teams.
The malware’s sophistication extends beyond traditional information stealing, incorporating advanced techniques such as Dead Drop Resolver (DDR) methods, direct syscall implementation, and WoW64 transition abuse to evade endpoint detection and response (EDR) systems.
Recent campaigns have demonstrated ACR Stealer’s ability to compromise over 200 applications across multiple categories, from cryptocurrency wallets to password managers, while maintaining persistent communication with threat actor infrastructure through ingeniously disguised channels.
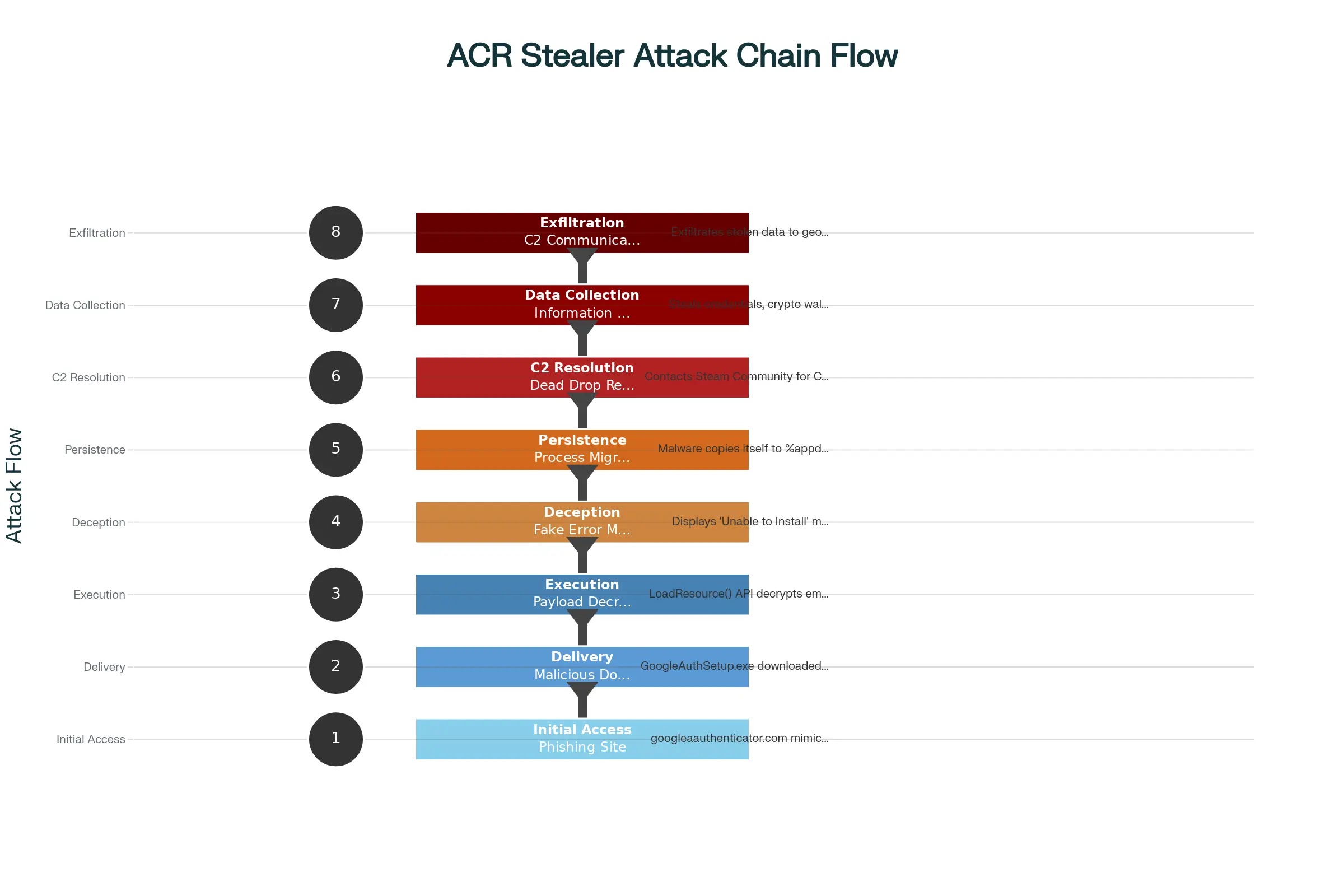
ACR Stealer Attack Chain
ACR Stealer campaigns typically initiate through sophisticated phishing operations that leverage social engineering to deceive victims into executing malicious payloads.
The most extensively documented attack vector involves a fraudulent website masquerading as an official Google Safety Centre, hosted at “googleaauthenticator[.]com”.
This phishing site meticulously replicates Google’s branding and interface design to establish credibility with potential victims.
When victims interact with the “Download Authenticator” button on the malicious site, they unknowingly trigger the download of “GoogleAuthSetup.exe” from “hxxps://webipanalyzer[.]com/GoogleAuthSetup.exe”.
This initial payload serves as a sophisticated loader that employs several deception techniques to mask its malicious nature. The executable features a valid digital signature, which helps bypass initial security screening by creating the appearance of legitimacy.
The loader’s architecture demonstrates advanced obfuscation through its use of encrypted payloads stored within the RCData section of the executable.
Upon execution, the malware leverages the LoadResource() API to extract and decrypt these embedded payloads, subsequently saving them to the system’s %temp% directory.
The decryption process reveals two distinct malware components: ACR Stealer and Latrodectus, each designed for specific malicious functions.
Process Injection And Persistence Mechanisms
ACR Stealer employs sophisticated process injection techniques that utilize direct syscalls to evade user-mode API monitoring.
The malware specifically uses the NtCreateUserProcess syscall to spawn child processes, bypassing traditional CreateProcess API calls that are commonly monitored by security solutions.
This technique represents a significant advancement in evasion capabilities, as many EDR systems rely on user-mode API hooks for detection.
The malware establishes persistence through multiple mechanisms, including scheduled task creation and strategic file placement. When executed from the temporary directory, the malware performs an environment check to determine its execution context.
If not running from the %appdata% directory, it copies itself to this location and re-executes from the new path before terminating the original process.
This behavior ensures the malware maintains a foothold on the system while removing evidence of its initial execution location.
Recent variants have incorporated advanced persistence techniques that leverage COM objects to create scheduled tasks configured for frequent execution.
Unlike earlier versions that only triggered at logon, newer iterations schedule execution every 10 minutes, demonstrating an evolution toward more aggressive persistence strategies.
Technical Capabilities And Evasion Techniques
Dead Drop Resolver Implementation
One of ACR Stealer’s most notable innovations is its implementation of Dead Drop Resolver (DDR) techniques to obfuscate command-and-control infrastructure.
This method represents a significant advancement over traditional C2 communication by embedding server details within legitimate platforms that security tools are unlikely to flag as suspicious.
The malware leverages multiple platforms for DDR implementation, including Steam Community profiles, Google Docs, and Telegram channels.
In documented campaigns, ACR Stealer accesses specific Steam Community profiles, such as “hxxps://steamcommunity[.]com/profiles/76561199679420718,” to retrieve encoded C2 server information.
This approach provides operational security benefits by allowing threat actors to dynamically change C2 infrastructure without updating malware samples.
The DDR process involves multiple stages of encoding and decoding. The malware first contacts the legitimate platform to extract encoded data, typically using Base64 encoding with additional XOR encryption layers.
After retrieving the encoded information, ACR Stealer constructs the actual C2 URL and proceeds to download encrypted configuration files that contain targeting parameters and operational instructions.
Advanced Communication Protocols
ACR Stealer has evolved to incorporate sophisticated communication mechanisms that bypass traditional network monitoring solutions.
Recent variants implement NTSockets functionality, which interfaces directly with the Windows AFD (Auxiliary Function Driver) device rather than using standard Winsock libraries.
This technique enables the malware to establish network communications while evading EDR systems that rely on user-mode API hooking for network traffic monitoring.
The NTSockets implementation involves direct communication with the “DeviceAfdEndpoint” device using low-level NT functions such as NtCreateFile and NtDeviceIoControlFile.
This approach effectively bypasses almost all commonly used Windows networking APIs that security solutions monitor for HTTP requests.
The malware constructs HTTP requests manually at the protocol level, assembling headers and payloads without relying on higher-level libraries.
WoW64 And Heaven’s Gate Exploitation
Advanced ACR Stealer variants employ Heaven’s Gate techniques to execute 64-bit code within 32-bit processes, further complicating detection and analysis.
This technique exploits the WoW64 subsystem to transition between 32-bit and 64-bit execution modes, allowing the malware to access extended functionality while maintaining compatibility with older systems.
The Heaven’s Gate implementation involves direct manipulation of the processor’s execution mode through carefully crafted assembly code that transitions from 32-bit to 64-bit mode.
This technique is particularly effective against analysis tools and sandboxes that may not properly handle mode transitions.
The malware uses this capability to execute critical functions such as C2 communication while disrupting automated analysis systems.
Data Stealing Operations
ACR Stealer demonstrates unprecedented scope in its data harvesting capabilities, targeting over 200 applications across eight major categories.
The malware’s targeting strategy reflects a comprehensive understanding of modern digital asset management and communication patterns.
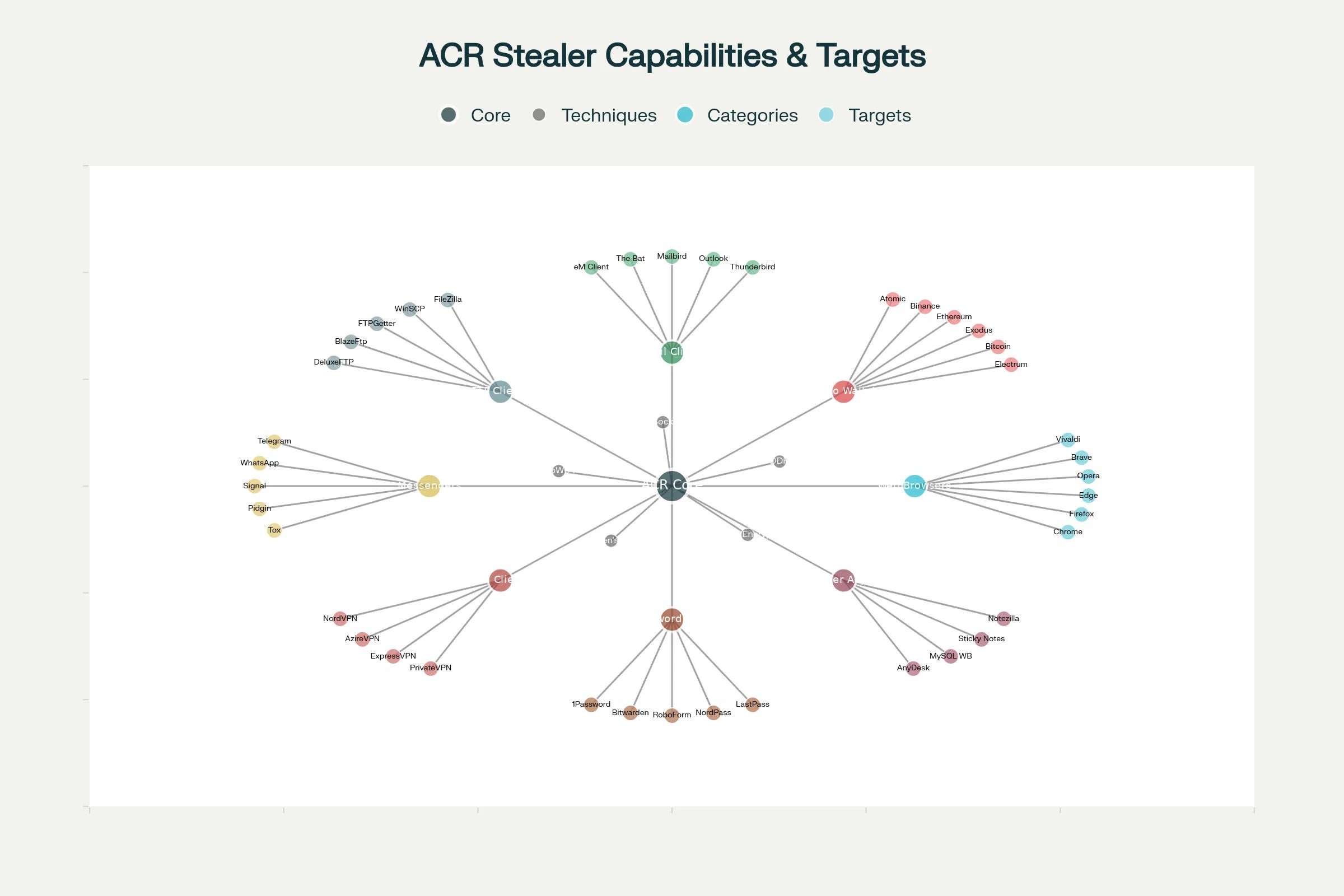
Web Browser Exploitation: The malware targets an extensive array of web browsers, including mainstream options like Chrome, Firefox, and Edge, as well as privacy-focused alternatives such as Brave and specialized browsers like Opera GX.
ACR Stealer extracts stored credentials, cookies, autofill data, browsing history, and session tokens from these applications.
Recent variants have developed capabilities to bypass Chrome’s App Bound Encryption by injecting shellcode directly into browser processes.
Cryptocurrency Wallet Targeting: ACR Stealer exhibits a sophisticated understanding of the cryptocurrency ecosystem, targeting over 50 different wallet applications.
The malware specifically seeks wallet.dat files, private keys, seed phrases, and configuration files from applications including Electrum, Exodus, Bitcoin Core, Ethereum wallets, and hardware wallet management software.
This comprehensive approach to cryptocurrency theft reflects the high-value nature of digital assets in cybercriminal operations.
Enterprise Communication Tools: The malware targets email clients such as Thunderbird, Outlook, Mailbird, and specialized applications like The Bat!.
Additionally, it harvests data from FTP clients, including FileZilla, WinSCP, and various commercial FTP applications.
This targeting strategy suggests a focus on compromising business communications and file transfer credentials that could enable lateral movement or business email compromise attacks.
Data Exfiltration And Processing
ACR Stealer implements sophisticated data processing mechanisms that organize harvested information into structured formats suitable for threat actor consumption.
The malware categorizes stolen data by application type and implements compression algorithms to optimize transmission efficiency.
The exfiltration process involves multiple encryption layers, including XOR encoding with hardcoded keys and Base64 encoding for protocol compatibility.
Stolen data is transmitted to C2 servers using HTTP POST requests with carefully crafted headers designed to blend with legitimate web traffic.
The malware implements error-handling mechanisms to ensure data integrity during transmission and includes retry logic for failed uploads.
Command And Control Infrastructure
Dynamic C2 Resolution
ACR Stealer’s C2 infrastructure demonstrates remarkable resilience through its implementation of dynamic resolution mechanisms.
Rather than relying on hardcoded IP addresses or domains, the malware retrieves C2 information from legitimate platforms that are unlikely to be blocked by network security solutions.
The configuration retrieval process involves accessing URLs such as “hxxps://geotravelsgi[.]xyz/ujs/2ae977f4-db12-4876-9e4d-fc8d1778842d” to download encrypted configuration files.
These configurations contain not only C2 server details but also targeting parameters, update mechanisms, and additional payload delivery instructions.
Multi-Stage Payload Delivery
Recent ACR Stealer variants have incorporated multi-stage payload delivery capabilities that enable threat actors to deploy additional malware based on victim value or operational requirements.
The malware’s configuration includes a “loader” key that specifies secondary payloads for execution. These payloads can be delivered as executable files, PowerShell scripts, or DLL libraries, depending on the threat actor’s objectives.
The secondary payload execution system supports various file type,s including .exe, .cmd, .dll, and .ps1 files.
For PowerShell-based payloads, the malware implements DownloadString and Invoke-Expression (IEX) execution methods.
This flexibility enables threat actors to adapt their operations based on the victim environment and value assessment.
Indicators Of Compromise
| Indicator Type | Indicator Value | Description |
|---|---|---|
| SHA256 | 532c9bc2e30150bef61a050386509dd5f3c152688898f6be616393f10b9262d3 | ACR Stealer payload |
| SHA256 | 62536e1486be7e31df6c111ed96777b9e3f2a912a2d7111253ae6a5519e71830 | GoogleAuthSetup.exe loader |
| SHA256 | 81bc69a33b33949809d630e4fa5cdb89d8c60cf0783f447680c3677cae7bb9bb | Latrodectus payload |
| Domain | googleaauthenticator.com | Phishing site mimicking Google |
| Domain | geotravelsgi.xyz | C2 server for configuration |
| URL | https://webipanalyzer[.]com/GoogleAuthSetup.exe | Malware download URL |
| URL | https://geotravelsgi[.]xyz/ujs/2ae977f4-db12-4876-9e4d-fc8d1778842d | ACR Stealer config URL |
| URL | https://steamcommunity[.]com/profiles/76561199679420718 | DDR on Steam Community |
| URL | https://spikeliftall[.]com/live/ | Latrodectus C2 |
| URL | https://godfaetret[.]com/live/ | Latrodectus C2 |
| File Path | %temp%[random].exe | ACR Stealer temp location |
| File Path | %appdata%[random].exe | ACR Stealer persistence location |
| Registry Key | HKCUSoftwareMicrosoftWindowsCurrentVersionRun | Persistence registry key |
| User-Agent | Mozilla/5.0 (Windows NT 10.0; Win64; x64) | Common HTTP User-Agent |
| HTTP Method | POST | Data exfiltration method |
| Content-Type | application/x-www-form-urlencoded | HTTP content type |
| Mutex | GlobalACR_* | ACR Stealer mutex pattern |
| Process Name | GoogleAuthSetup.exe | Initial loader process |
| Service Name | Windows Update Service | Fake service name |
| Bitcoin Address | bc1q* | Potential crypto wallet (pattern) |
| API Call | NtCreateUserProcess | Process creation syscall |
| API Call | NtCreateFile | File operations |
| API Call | NtDeviceIoControlFile | Direct AFD communication |
| DLL | ntdll.dll | Direct syscall implementation |
| DLL | wow64cpu.dll | WoW64 transition DLL |
ACR Stealer has evolved into a more sophisticated variant known as Amatera Stealer, which incorporates significant improvements in evasion capabilities and operational security.
This rebranded version maintains core ACR Stealer functionality while introducing enhanced anti-analysis features and improved sophistication.
Amatera Stealer represents active development efforts to counter security improvements and maintain operational effectiveness.
The evolution includes abandoning Steam and Telegram dead drops in favor of direct C2 connections with hardcoded IP addresses. This change suggests adaptation to detection methods while maintaining operational capabilities.
The ACR Stealer family demonstrates continuous development patterns that reflect active threat actor investment in maintaining operational effectiveness.
Updates include encryption key pattern modifications, new command implementations, and persistence mechanism enhancements.
These developments suggest well-resourced threat actors with long-term operational objectives.
Recent variants have introduced interesting anti-analysis features designed to complicate reverse engineering and automated analysis.
These include environment detection mechanisms, sandbox evasion techniques, and analysis disruption methods. The consistent addition of new features indicates ongoing development investment and threat evolution.
Mitigations
Security organizations defending against ACR Stealer must implement comprehensive, multi-layered approaches that address the malware’s sophisticated evasion techniques.
Network monitoring should focus on detecting DDR communications through behavioral analysis rather than relying solely on signature-based detection.
Endpoint protection should incorporate behavioral analysis capabilities that can identify direct syscall abuse and process injection techniques.
User education programs must emphasize the risks associated with downloading software from non-official sources and clicking on suspicious advertisements.
Organizations should implement strict software installation policies and provide official channels for legitimate software acquisition.
Additionally, implementing application allowlisting can prevent execution of unauthorized software, including ACR Stealer variants.
The sophistication of ACR Stealer and its variants represents a significant challenge for cybersecurity professionals, requiring advanced detection capabilities and comprehensive security strategies to effectively counter this evolving threat.
As threat actors continue developing more sophisticated techniques, security teams must remain vigilant and adapt their defensive strategies to address these advancing capabilities.
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant Updates.