A new report from Recorded Future’s Insikt Group reveals that the Chinese state-sponsored threat group RedNovember has significantly broadened its operations, striking across government, defense, aerospace, and technology sectors worldwide. The group, previously tracked as TAG-100 and overlapping with Storm-2077, continues to exploit in internet-facing devices to gain stealthy initial access.
According to Insikt Group, “In July 2024, Insikt Group publicly reported on TAG-100, a threat activity group conducting suspected cyber-espionage activity… after reviewing all available evidence, we assess that TAG-100 is highly likely a Chinese state-sponsored threat activity group. Accordingly, Insikt Group now tracks this group under the designation RedNovember.”
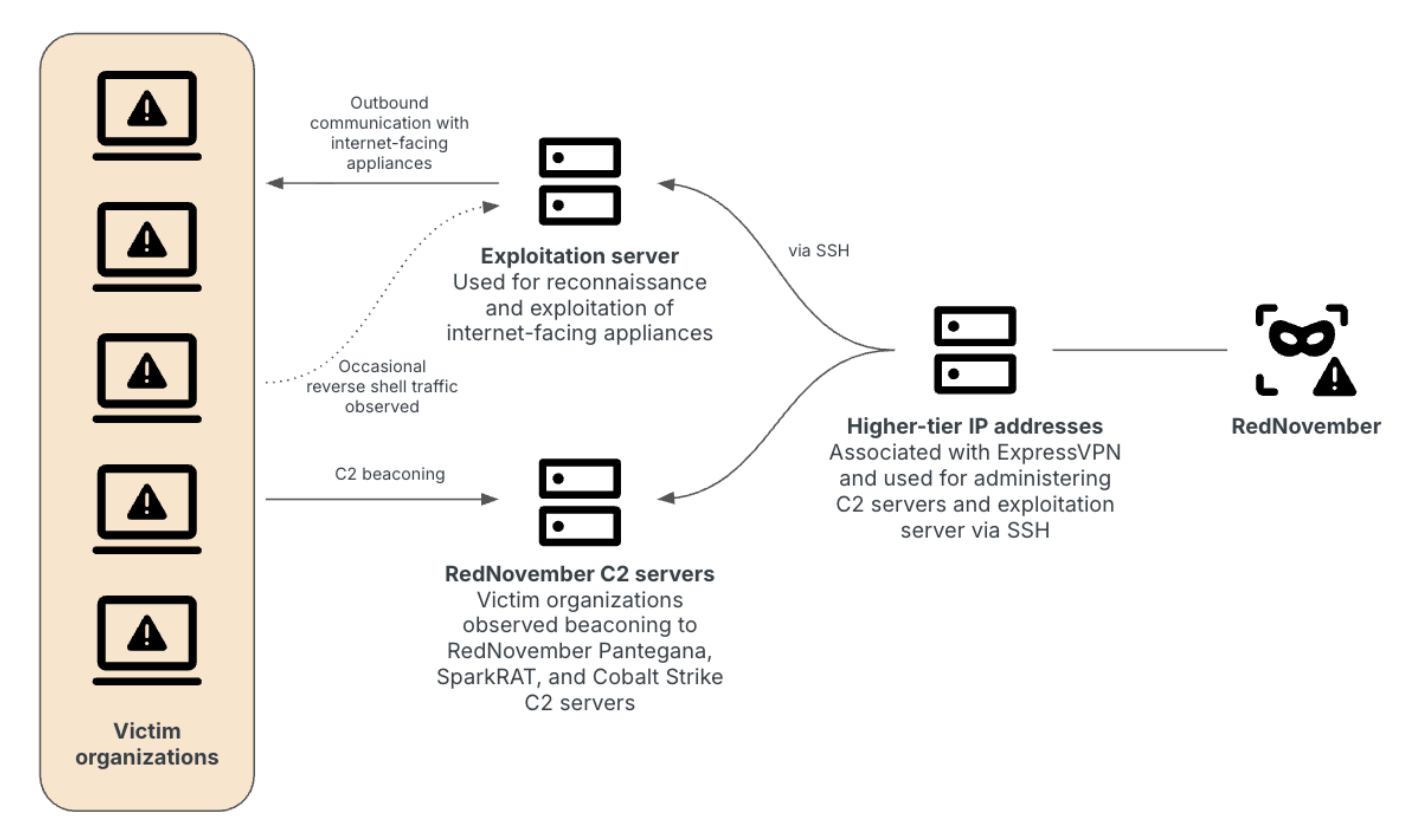
Between June 2024 and July 2025, RedNovember has consistently used the Go-based backdoor Pantegana, Cobalt Strike, and more recently SparkRAT, leveraging these tools for reconnaissance, lateral movement, and persistent command-and-control.
The group has widened its targeting remit beyond traditional government and diplomatic bodies. The report states, “RedNovember has significantly broadened its targeting to include the US defense industrial base, aerospace, and high-technology manufacturing verticals, including semiconductors.”
Key victims identified include:
- A ministry of foreign affairs in Central Asia.
- A state organization in Africa.
- A European government directorate.
- Multiple Southeast Asian government agencies.
- At least two US defense contractors and a European engine manufacturer.
The campaign also extended to law firms, Taiwanese semiconductor firms, European manufacturing, and even US oil and gas companies.
RedNovember has adopted an opportunistic exploitation model. Insikt Group observed, “We observed RedNovember reconnoitering and likely compromising edge devices for initial access, including SonicWall, Cisco ASA, F5 BIG-IP, Palo Alto GlobalProtect, Sophos SSL VPN, and Fortinet FortiGate instances, as well as Outlook Web Access (OWA) instances and Ivanti Connect Secure VPN appliances.”
The group rapidly exploits newly released . For example, following the publication of a proof-of-concept exploit for CVE-2024-24919 (Check Point VPN gateways), RedNovember was observed scanning and likely attempting exploitation within days.
Beyond edge exploitation, RedNovember relies on LESLIELOADER, an open-source Go-based loader, to deploy SparkRAT and Cobalt Strike. In one campaign, the loader was disguised as a VMware patch, even embedding the specific name of a US Navy contractor to improve targeting fidelity.
Insikt Group links RedNovember’s campaigns to geopolitical flashpoints. For example:
- In Taiwan, RedNovember reconnaissance coincided with large-scale Chinese military exercises, focusing on semiconductor R&D organizations and an air force base.
- In Panama, over 30 government entities were targeted shortly after the US announced an expanded security partnership to counter Chinese influence in the Panama Canal.
- In South Korea, RedNovember probed nuclear safety organizations and telecom companies, aligning with regional strategic interests.
- These operations suggest that RedNovember’s tasking is closely tied to China’s military, economic, and foreign policy priorities.
Insikt Group warns, “RedNovember, along with other Chinese state-sponsored threat activity groups, will almost certainly continue to target edge devices and exploit vulnerabilities soon after their release.”
To defend against such activity, organizations are urged to:
- Prioritize patching perimeter appliances and services.
- Monitor for communication with known Pantegana, SparkRAT, and Cobalt Strike C2 infrastructure.
- Harden and segment networks to reduce impact of edge compromises.
- Detect post-exploitation tactics such as web shells, backdoors, and lateral movement.
- SparkRAT: A Persistent Cross-Platform Cyber Threat Targeting macOS and Beyond
- Stealthy New Loader Helps SPARKRAT Malware Evade Detection
- Threat Actors Exploit GitHub to Spread Malware, Targeting Multiple Operating Systems
- TAG-100’s Global Espionage Campaign: Exploiting Open-Source Tools
- Google exposes a Microsoft Edge browser flaw