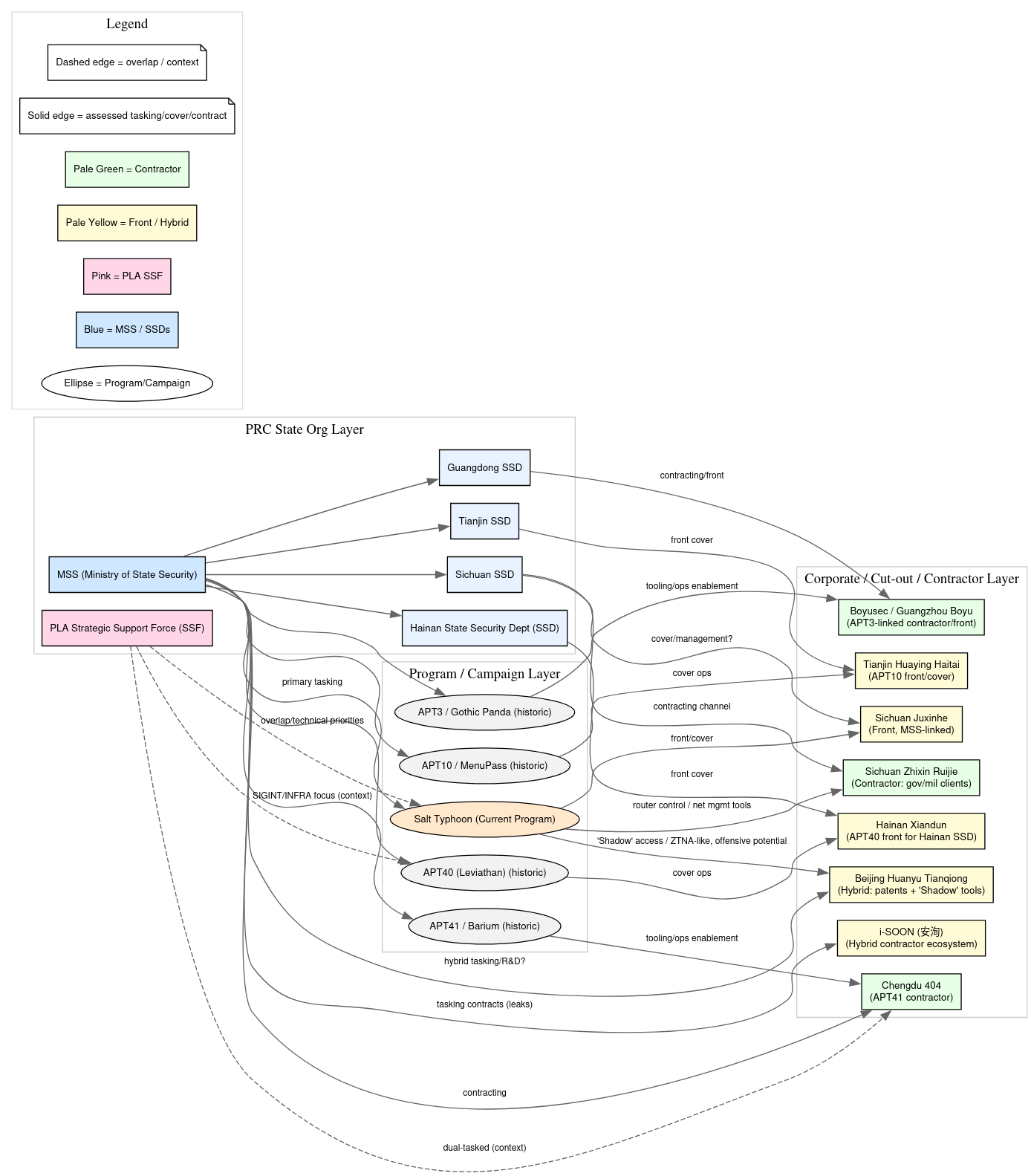
In late 2024, a new wave of cyber espionage emerged targeting global telecommunications infrastructure. Operating under the moniker Salt Typhoon, this Chinese state-sponsored group has focused its efforts on routers, firewalls, VPN gateways, and lawful intercept systems within major telecom providers.
By embedding bespoke firmware implants and leveraging living-off-the-land binaries, Salt Typhoon has achieved persistent access capable of siphoning sensitive communications metadata, VoIP configurations, and subscriber profiles.
The group’s objectives align with strategic Chinese intelligence priorities: signals intelligence (SIGINT) collection, counterintelligence support, and preparation of potential cyber disruption operations.
Salt Typhoon campaigns exploit both public-facing vulnerabilities in network edge devices and misconfigurations in management interfaces. Initial access is typically gained through exploitation of router web interfaces, such as CVE-2023-20198 on Cisco IOS XE and CVE-2023-35082 in Ivanti Connect Secure appliances.
After breaching these devices, the adversary deploys a custom firmware rootkit—internally dubbed Demodex—which survives reboots and evades standard detection mechanisms.
Domaintools analysts identified distinctive domain registration patterns supporting Salt Typhoon’s infrastructure, noting the use of fabricated U.S. personas and ProtonMail accounts for WHOIS entries, an unusual lapse in operational security for a state-sponsored actor.
Once implanted, the malware establishes encrypted command-and-control channels over DNS beacons or HTTPS on TCP port 443.
Regular beacon intervals are disguised as routine firmware update checks, blending into normal network traffic. Exfiltrated data includes lawful intercept logs, call detail records (CDRs), and configuration dumps from edge routers.
Telecommunications providers in the United States, United Kingdom, and several European nations have reported unusual outbound traffic consistent with these implants, enabling the MSS (Ministry of State Security) to harvest high-value intelligence on user communications patterns and network topologies.
Operation impact
The impact of these operations extends beyond raw data theft. Long-dwell persistence in critical devices grants the attackers the ability to sabotage or reroute communications during geopolitical crises.
By maintaining backdoor access to core routers, Salt Typhoon can disrupt SIP traffic or inject false routing entries, potentially degrading service or enabling additional espionage within allied defense and government networks.
This blend of espionage and contingency planning underscores the dual-use nature of the campaign: everyday intelligence collection complemented by latent offensive capabilities.
A deeper look at Infection Mechanism reveals the precision of Salt Typhoon’s exploitation and implant deployment.
The group’s engineers have crafted a minimalistic loader that leverages the router’s own command shell to write malicious binaries into /usr/bin/ and modify startup scripts.
For instance, a typical persistence snippet injected into a Juniper device’s configuration might appear as:-
# Inject persistence into startup script
echo "/usr/bin/demodex_loader &" >> /etc/rc.d/rc.local
chmod +x /usr/bin/demodex_loader
/usr/bin/demodex_loader --install --target=/dev/mtd0This code writes the loader invocation into the router’s boot sequence and flashes the rootkit into flash memory. The loader verifies the firmware version and selects the appropriate memory offsets to avoid bricking the device.
Once executed, Demodex hooks low-level system calls to intercept configuration reads and hide its presence, ensuring subsequent firmware updates cannot remove it without manual intervention.
By combining targeted exploitation of known CVEs, stealthy firmware implants, and contractor-enabled domain infrastructure, Salt Typhoon represents a sophisticated example of China’s evolving cyber espionage capabilities against telecommunications networks.
The campaign’s operational model—outsourced infrastructure provisioning paired with state-directed tasking—poses significant challenges for attribution and defense, but also offers defenders opportunities to disrupt emerging domains and certificate pivots before active exploitation begins.
Follow us on Google News, LinkedIn, and X to Get More Instant Updates, Set CSN as a Preferred Source in Google.



