Researchers at Darktrace have identified a sophisticated new campaign that merges traditional malware techniques with modern DevOps practices. Dubbed ShadowV2, this operation leverages GitHub CodeSpaces, Docker containers, and a Go-based RAT to deliver powerful DDoS-as-a-service capabilities.
According to Darktrace, “At the center of this campaign is a Python-based command-and-control (C2) framework hosted on GitHub CodeSpaces. This campaign also utilizes a Python-based spreader with a multi-stage Docker deployment as the initial access vector.”
What sets ShadowV2 apart is the sophistication of its design. The attackers combined DDoS techniques with targeted exploitation capabilities. The report notes, “The threat actors employ advanced methods such as HTTP/2 rapid reset, a Cloudflare under attack mode (UAM) bypass, and large-scale HTTP floods, demonstrating a capability to combine distributed denial-of-service (DDoS) techniques with targeted exploitation.”
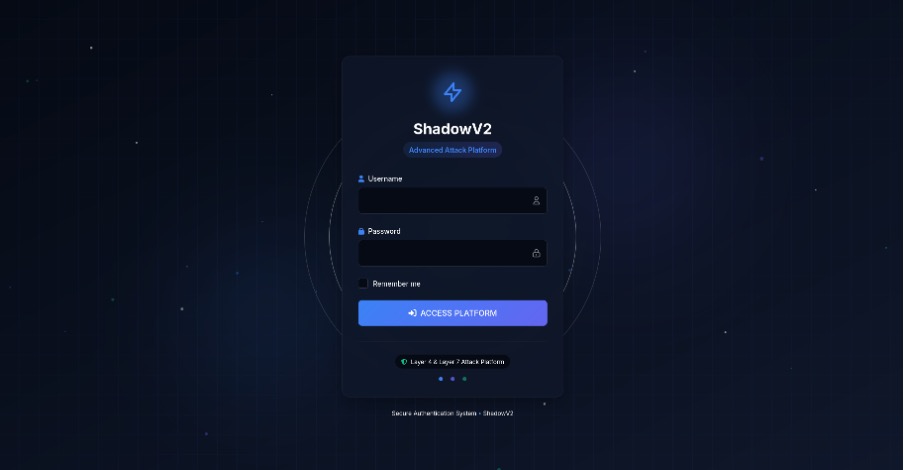
Unlike older botnets, ShadowV2 mimics the design of legitimate cloud-native applications. With its FastAPI and Pydantic-based OpenAPI specification, operator login panel, and admin/user privilege system, the infrastructure resembles a commercial SaaS product. As Darktrace explains, “the infrastructure seems to resemble a ‘DDoS-as-a-service’ platform rather than a traditional botnet.”
The attackers specifically targeted Docker daemons running on AWS EC2. By abusing misconfigured instances with exposed Docker APIs, they could spawn containers directly on victim environments.
Darktrace observed: “This campaign targets exposed Docker daemons, specifically those running on AWS EC2… it first spawns a generic ‘setup’ container and installs a number of tools within it. This container is then imaged and deployed as a live container with the malware arguments passed in via environmental variables.”
This approach reduces forensic footprints, as much of the build process occurs on the victim’s infrastructure.
Inside the deployed container sits an unstripped Go binary, which makes analysis easier but execution far more dangerous for victims. The malware phones home using a RESTful API, registering with a VPS_ID derived from environment variables and polling every few seconds for new commands.
The RAT supports advanced DDoS operations, including multi-threaded HTTP floods using the high-performance fasthttp library. As the report notes, “The malware then spins up several threads, each running a configurable number of HTTP clients… to perform an HTTP flood attack against the target.”
Optional flags allow the malware to enable evasion techniques such as random query strings, spoofed IP headers, and a Cloudflare UAM bypass using ChromeDP to solve JavaScript challenges.
Perhaps the most alarming discovery was the publicly accessible Swagger UI left exposed by the attackers. Darktrace researchers were able to obtain full API documentation, revealing multi-tenant capabilities for customers.
“It is very likely a DDoS-for-hire platform (or at the very least, designed for multi-tenant use) based on the extensive user API, which features authentication, distinctions between privilege level (admin vs user), and limitations on what types of attack a user can execute.”
The login panel, styled with Tailwind and animations, even branded itself as an “advanced attack platform”, highlighting the professionalization of cybercrime infrastructure.
ShadowV2 demonstrates how cybercriminals are adopting cloud-native engineering practices to build scalable, modular attack frameworks. As Darktrace concludes, “By leveraging containerization, an extensive API, and with a full user interface, this campaign shows the continued development of cybercrime-as-a-service.”
- CVE-2024-52308: GitHub CLI Vulnerability Could Allow Remote Code Execution
- DieNet Hacktivist Group Exploits DDoS-as-a-Service in Rapid Attacks
- Darktrace Exposes “Fake Startup” Malware Campaign: Lures Crypto Users with AI/Web3 Apps to Steal Wallets
- SocGholish Reloaded: Darktrace Uncovers Ransomware-Primed Loader Campaign
- Broadcom & Canonical Join Forces to Supercharge AI and Cloud with Ubuntu