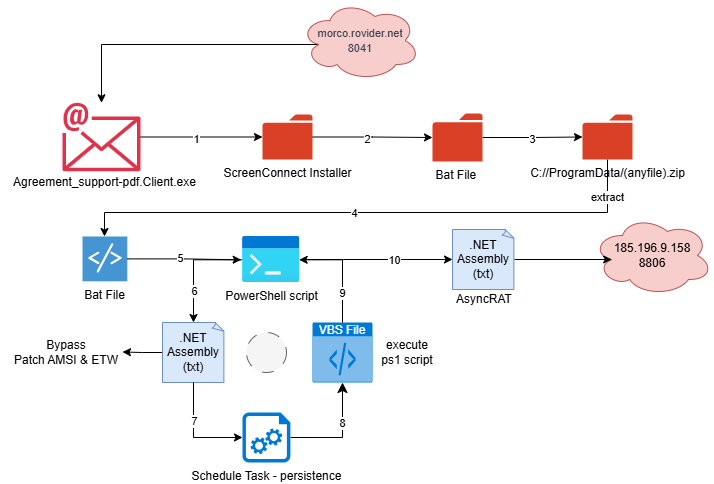
A new report from Hunt Intelligence reveals how attackers are abusing ConnectWise ScreenConnect (formerly ConnectWise Control) to deliver AsyncRAT and custom malware payloads. By leveraging trojanized installers, open directories, and phishing lures, adversaries have transformed a trusted remote monitoring and management (RMM) tool into a malware delivery vector with serious supply chain implications.
According to the report, “Remote Monitoring and Management (RMM) tools like ConnectWise ScreenConnect have become both indispensable for IT administrators and highly attractive to threat actors… ScreenConnect’s deep system access, trusted installation footprint, and widespread use across managed service providers make it a prime vector for malware delivery and persistence.”
Investigators uncovered at least eight infrastructure hosts staging ScreenConnect installers linked to AsyncRAT activity. These open directories contained suspicious archives such as aA.zip and 99.zip, which unpack into malicious toolkits including Ab.vbs, Skype.ps1, libPK.dll, and Microsoft.lnk.
The report highlights, “this blending of remote management software abuse with commodity RAT delivery highlights both a supply-chain risk and the operational tradecraft adversaries use to evade traditional signature-based defenses.”
Key findings included:
- Payload containers with filenames like logs.ldk, logs.idk, and logs.idr.
- Some hashes were completely undetected on VirusTotal, indicating fresh repackaging.
- Frequent use of /Bin/ directories across phishing domains to stage executables.
The attackers deploy AsyncRAT alongside a custom PowerShell RAT, ensuring redundancy and persistence. Hunt notes, “Payloads observed: AsyncRAT and a custom PowerShell RAT were deployed alongside trojanized ScreenConnect installers.”
Execution strategies vary depending on the environment:
- In-memory execution via .NET Assembly.Load for machines with antivirus protection.
- Native injection through libPK.dll::Execute in unprotected environments.
- Persistence is achieved with scheduled tasks such as SystemInstallTask and 3losh, which run every 2–10 minutes, making removal difficult.
The campaign also leverages phishing redirects masquerading as job or document portals. For example, one chain begins with police.html, redirects through galusa.ac.mz, and lands on dual.saltuta.com, which hosts payloads like event_support-pdf.Client.exe.
The report explains, “the /Bin/ ClickOnce pattern (from police.html → galusa.ac.mz → dual.saltuta.com) produced 8 related URLs across 2024–2025 during dataset queries.”
Analysis of IP addresses (e.g., 176.65.139.119, 45.74.16.71, 164.68.120.30) revealed long-lived AsyncRAT C2 servers with wide port rotations.
Hunt Intelligence observed, “AsyncRAT telemetry spans standard ports (21/80/111/443) and numerous high-ephemeral ports (30,000–60,000), often TLS-wrapped.”
This resilience suggests a builder-driven, automated deployment system designed for long-term persistence rather than opportunistic attacks.
The findings build on previous disclosures from Acronis, CyberProof, and Proofpoint, which also reported campaigns using trojanized ScreenConnect installers. Notably, in May 2025, ConnectWise confirmed a breach of its cloud-hosted ScreenConnect infrastructure, tied to CVE-2025-3935, a critical ViewState injection flaw.
The report warns that attackers are even experimenting with Authenticode stuffing, modifying certificate tables in malicious installers while preserving valid digital signatures to bypass trust checks.
- Critical Security Vulnerabilities in ConnectWise ScreenConnect Demand Immediate Patching
- CISA Adds 5 Actively Exploited Vulnerabilities to KEV Catalog: ASUS Routers, Craft CMS, and ConnectWise Targeted
- ConnectWise ScreenConnect Targeted by Nation-State Actor
- ConnectWise Patches Critical ViewState RCE Vulnerability in ScreenConnect
- Acronis TRU Uncovers Surge in ScreenConnect Abuse with Dual-RAT Deployment