Security researcher Volticks has published a deep technical writeup on CVE-2025-21692, a vulnerability in the Linux kernel’s Enhanced Transmission Selection (ETS) qdisc that can be exploited to gain powerful kernel-level primitives and ultimately remote code execution (RCE).
In the researcher’s own words, “Enter stage left, CVE-2025-21692. The bug in question is present in the ETS (Enhanced Transmission Selection) qdisc. ETS is classful and gets pretty complicated, as you can imagine. The bug, by comparison is very simple.”
The bug arises from a logic flaw in the ets_class_from_arg function, where improper validation of the class identifier leads to an out-of-bounds access. Volticks explains:
“As the patch hints, the arg class id can be 0, and if it is we can probably underflow and read OOB. There’s also a chance we can go higher, if we somehow feed this function an id greater than nbands.”
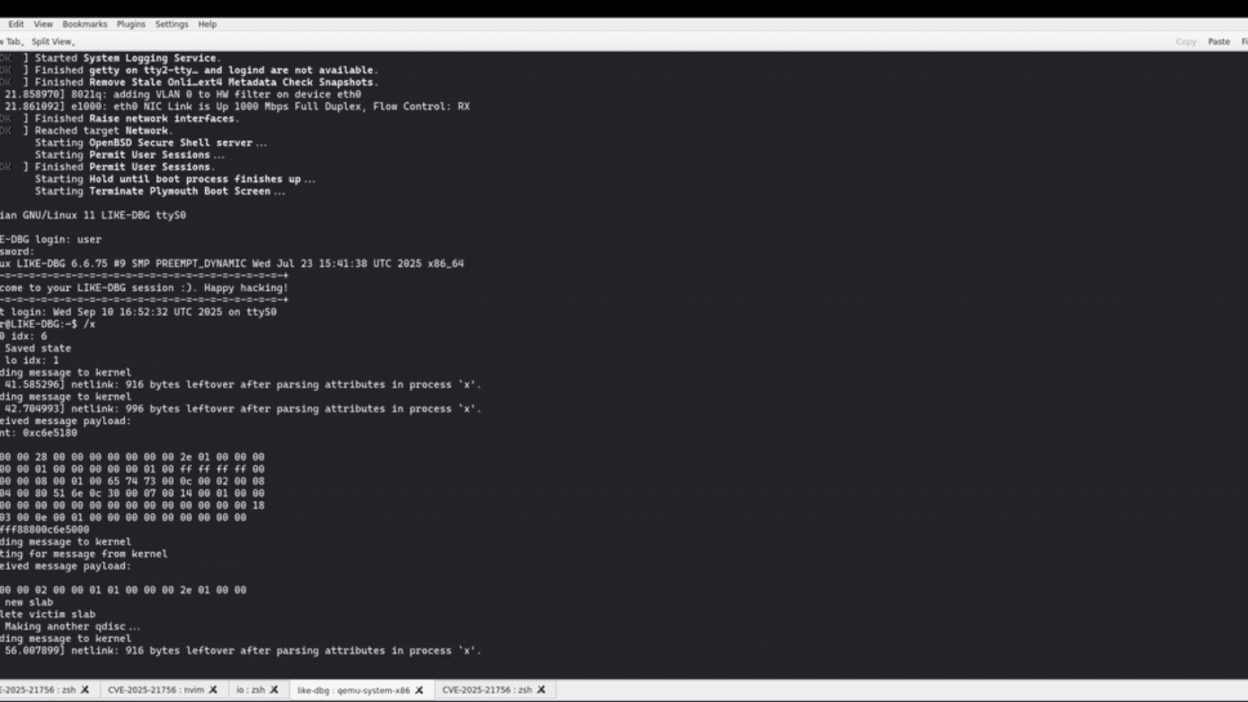
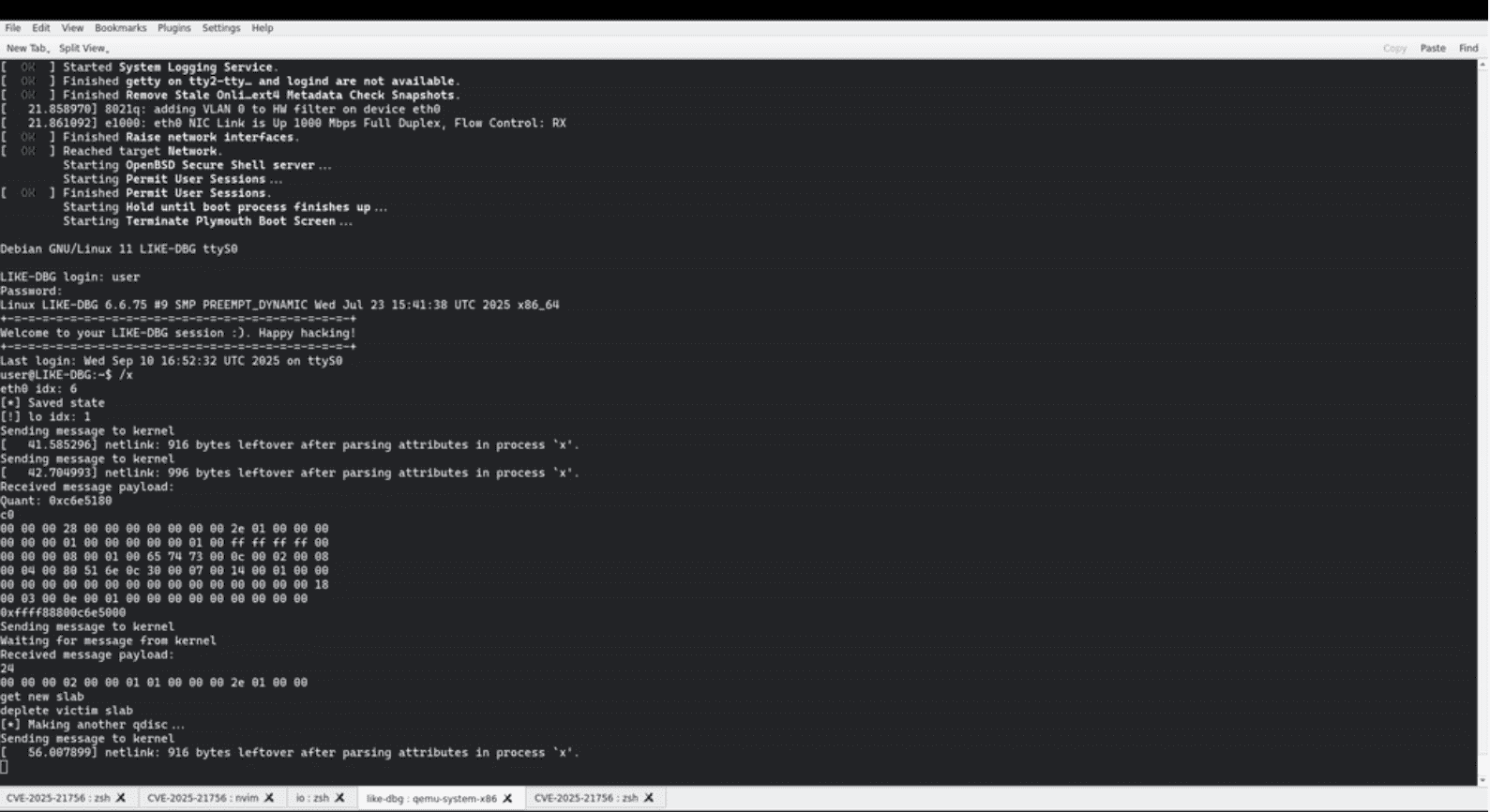
This underflow condition allows attackers to tamper with internal ETS structures, particularly the quantum field of classes, which plays a critical role in bandwidth scheduling. By manipulating this field, an attacker can corrupt memory structures and set the stage for further exploitation.
Volticks’ exploration focused on turning this out-of-bounds write into a reliable exploit primitive. By corrupting ETS class structures, the researcher discovered a way to overwrite kernel pointers, describing the process as:
“So basically we end up doing active->prev->next = &cl->alist, which is perfect for us (active->prev is controlled atp). Now, how do we trigger. Very very simple, just send a packet to the interface!”
This gave the exploit a write-what-where primitive, allowing carefully crafted writes into kernel memory.
To move from a memory corruption primitive to full exploitation, Volticks combined techniques such as cross-cache attacks, heap spraying, and message queue abuse. A critical breakthrough came when targeting PF_PACKET sockets:
“Enter stage right, PF_PACKET. This specific socket kind ends up in kmalloc-2k. So why and how can this object be leveraged for code execution? All struct socks have a certain member, skc_prot… This essentially acts as a family specific vtable of functions.”
By overwriting the skc_prot vtable with controlled data, the exploit hijacked execution flow. With a crafted ROP chain, the researcher achieved privilege escalation and arbitrary code execution in the kernel.
A proof-of-concept exploit is available on Github.