Introduction
Warlock is a ransomware strain operating under the Ransomware-as-a-Service (RaaS) model that emerged in June 2025, following an advertisement on the Russian Anonymous Marketplace (RAMP) with the tagline: “If you want a Lamborghini, please contact me.”
Although no direct lineage to prior ransomware families has been confirmed, Warlock exhibits similarities to Black Basta, a prolific ransomware operation that ceased publishing victim data in early 2025. Similarities in tactics, extortion strategies, and victimology suggest a possible offshoot or rebrand.
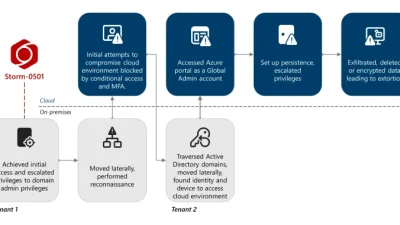
Warlock ransomware has been associated with the China-based adversary known as Storm-2603, which has deployed the ransomware in at least 11 confirmed incidents since mid-July 2025.
In these incidents, Warlock operators primarily targeted internet-exposed, unpatched on-premises Microsoft SharePoint servers, exploiting recently disclosed zero-day vulnerabilities, specifically CVE-2025-49704, CVE-2025-49706, CVE-2025-53770, and CVE-2025-53771, collectively referred to as the “ToolShell” exploit chain, enabling unauthenticated access and arbitrary command execution on vulnerable SharePoint instances.
On July 30, 2025, AttackIQ released an emulation that compiles the Tactics, Techniques, and Procedures (TTPs) associated with the exploitation of the CVE-2025-49704, CVE-2025-49706, CVE-2025-53770, and CVE-2025-53771 vulnerabilities, which affect on-premises Microsoft SharePoint servers.
AttackIQ has released a new attack graph that emulates the Tactics, Techniques, and Procedures (TTPs) associated with the deployment of Warlock ransomware to help customers validate their security controls and their ability to defend against this disruptive and destructive threat.
Validating your security program performance against these behaviors is vital in reducing risk. By using these new attack graphs in the AttackIQ Security Optimization Platform, security teams will be able to:
- Evaluate security control performance against baseline behaviors associated with the Warlock ransomware.
- Assess their security posture against an opportunistic adversary, which does not discriminate when it comes to selecting its targets.
- Continuously validate detection and prevention pipelines against a playbook similar to those of many of the groups currently focused on ransomware activities.
Malware Emulation
Warlock Ransomware – 2025-07 – Associated Tactics, Techniques and Procedures (TTPs)
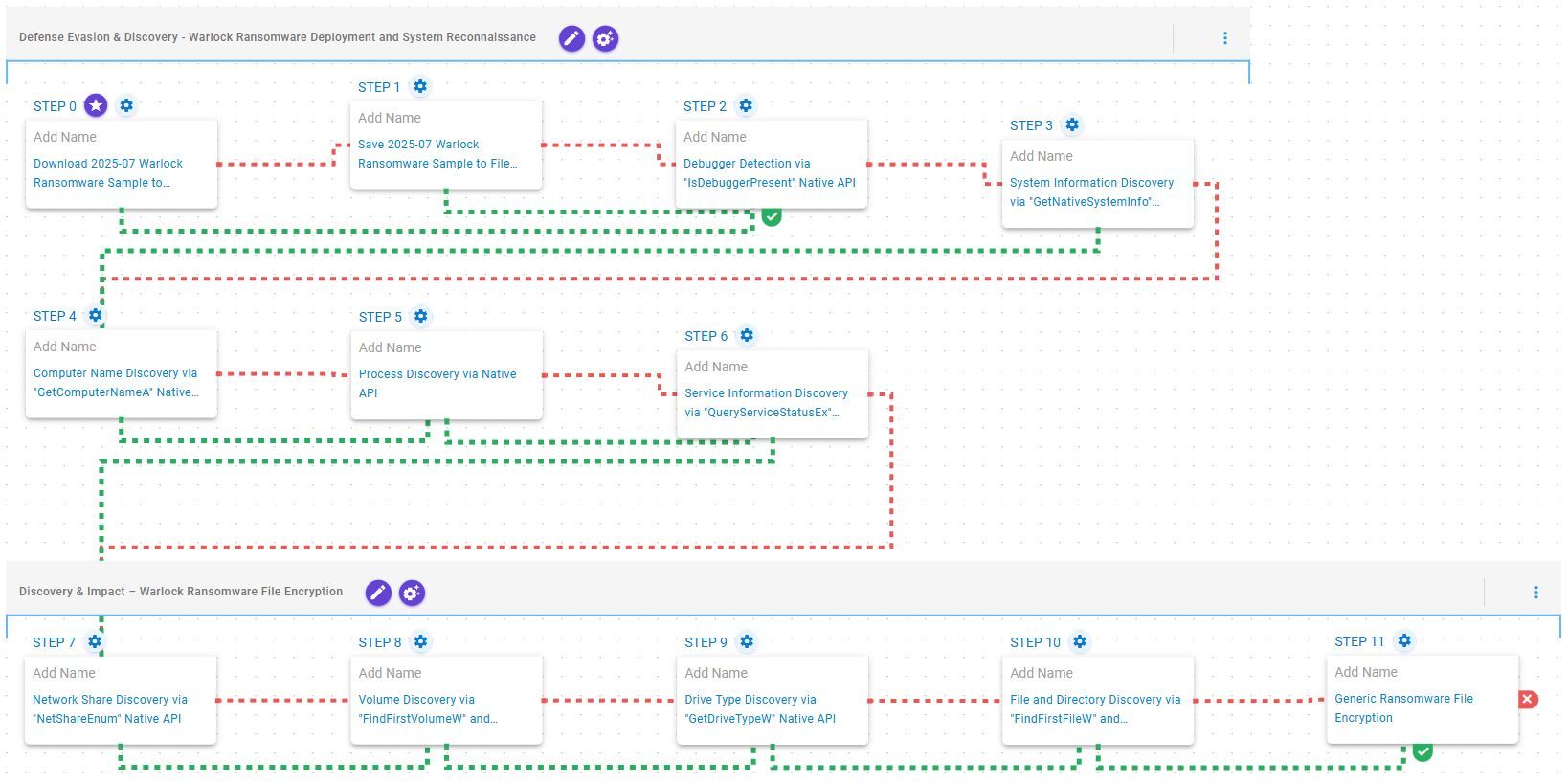
This emulation replicates the sequence of behaviors associated with the deployment of Warlock ransomware on a compromised system with the intent of providing customers with the opportunity to detect and/or prevent a compromise in progress.
The emulation is based on behaviors reported by Microsoft on July 22, 2025, Halcyon on July 25, 2025, and Trend Micro on August 20, 2025.
Defense Evasion & Discovery – Warlock Ransomware Deployment and System Reconnaissance
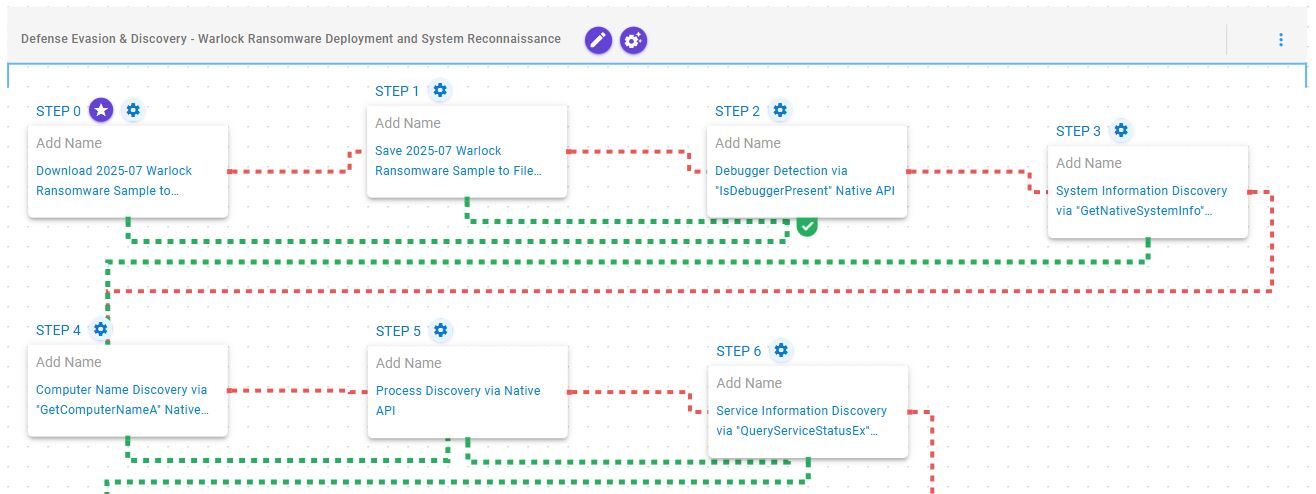
This stage begins with the deployment of Warlock ransomware which, once operational, performs debugger detection by executing the IsDebuggerPresent Windows API. Subsequently, it collects general system information via GetNativeSystemInfo, retrieves the computer name using GetComputerNameA, enumerates running processes through CreateToolhelp32Snapshot, Process32FirstW, and Process32NextW, and gathers service information via QueryServiceStatusEx and EnumDependentServices Windows APIs.
Ingress Tool Transfer (T1105): This scenario downloads to memory and saves to disk in independent scenarios to test network and endpoint controls and their ability to prevent the delivery of known malicious samples.
Virtualization/Sandbox Evasion (T1497): This scenario will execute the IsDebuggerPresent Windows API to detect the presence of a debugger attached to the current process.
System Information Discovery (T1082): This scenario executes the GetNativeSystemInfo Native API call to retrieve information associated to the system.
System Information Discovery (T1082): This scenario executes the GetComputerNameA Windows API call to retrieve a NetBIOS associated with the local computer.
Process Discovery (T1057): This scenario uses Windows API to receive a list of running processes by calling CreateToolhelp32Snapshot and iterating through each process object with Process32FirstW and Process32NextW.
System Service Discovery (T1007): This scenario executes the QueryServiceStatusEx and EnumDependentServices Windows API calls to retrieve information pertaining to a given service.
Discovery & Impact – Warlock Ransomware File Encryption
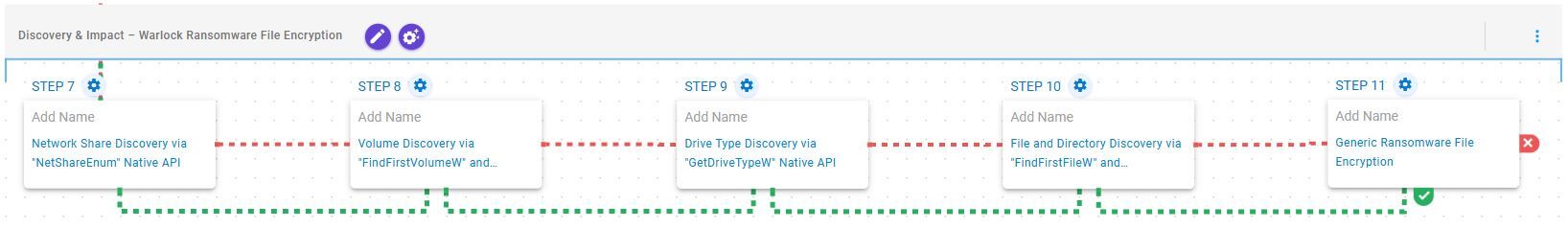
This stage begins with network share discovery using NetShareEnum, followed by volume enumeration via FindFirstVolumeW and FindNextVolumeW, and drive type identification through GetDriveTypeW. It then traverses the filesystem using FindFirstFileW and FindNextFileW. Finally, it encrypts the identified files using a combination of AES-256 in CBC mode for file encryption with RSA-2048 for key encryption.
Network Share Discovery (T1135): This scenario executes the NetShareEnum Windows native API call to enumerate network shares from the local computer.
System Information Discovery (T1082): This scenario executes the FindFirstVolumeW and FindNextVolumeW Windows API calls to iterate through the available volumes of the system.
System Information Discovery (T1082): This scenario executes the GetDriveTypeW Windows API call to retrieve information regarding the system’s physical drives.
File and Directory Discovery (T1083): This scenario will call the FindFirstFileW and FindNextFileW Windows API to perform the enumeration of the file system.
Data Encrypted for Impact (T1486): This scenario performs the file encryption routines used by common ransomware families. Files matching an extension list are identified and encrypted in place using similar encryption algorithms as used by multiple ransomware strains.
Wrap-up
In summary, this emulation will evaluate security and incident response processes and support the improvement of your security control posture against the behaviors exhibited by Warlock ransomware operators. With data generated from continuous testing and use of this assessment template, you can focus your teams on achieving key security outcomes, adjust your security controls, and work to elevate your total security program effectiveness against a known and dangerous threat.
AttackIQ, the leading provider of Adversarial Exposure Validation (AEV) solutions, is trusted by top organizations worldwide to validate security controls in real time. By emulating real-world adversary behavior, AttackIQ closes the gap between knowing about a vulnerability and understanding its true risk. AttackIQ’s AEV platform aligns with the Continuous Threat Exposure Management (CTEM) framework, enabling a structured, risk-based approach to ongoing security assessment and improvement. The company is committed to supporting its MSSP partners with a Flexible Preactive Partner Program that provides turn-key solutions, empowering them to elevate client security. AttackIQ is passionate about giving back to the cybersecurity community through its free award-winning AttackIQ Academy and founding research partnership with MITRE Center for Threat-Informed Defense.