

On August 26, 2025, Citrix announced a pivotal security update for NetScaler ADC and NetScaler Gateway appliances. This urgent patch addresses several high-impact vulnerabilities, including a critical remote code execution flaw (CVE-2025-7775) that is already being exploited. Organizations utilizing NetScaler products should review and apply the latest fixes immediately.
The New Vulnerabilities: What’s at Stake?
Citrix NetScaler appliances have recently come under attack due to new vulnerabilities. The most severe, CVE-2025-7775 (CVSS 9.2), enables unauthenticated remote code execution or denial-of-service when configured as a Gateway or AAA virtual server. Security researchers and Citrix have confirmed ongoing exploitation targeting these vulnerabilities. This vulnerability has been added to the KEV catalog following the exploitation attempts.
Additional vulnerabilities patched in this update include:
- CVE-2025-7776: Memory overflow leading to denial-of-service.
- CVE-2025-8424: Improper access control on the Management Interface.
Affected Versions and Released Fixes
If your environment includes any of the following NetScaler builds or older, you are at risk:
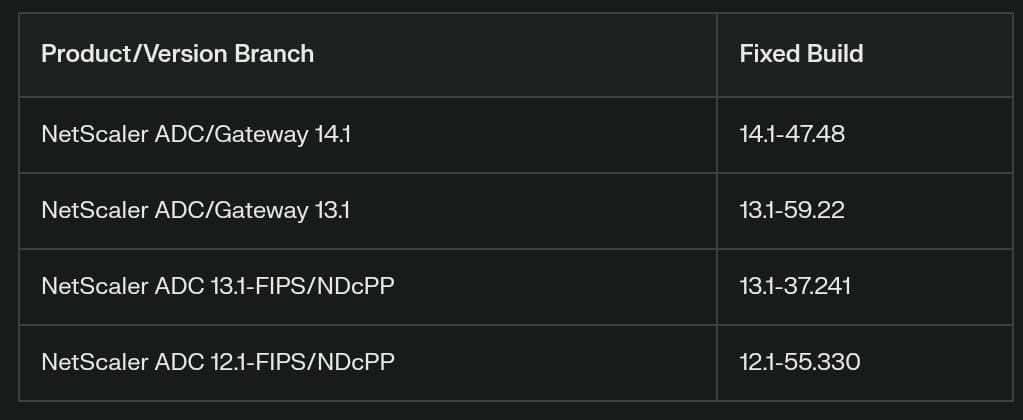
Older builds in these branches remain vulnerable, especially those configured as Gateway, AAA, or exposing the Management Interface.
Why Patch NOW?
- Active Exploitation: Attackers are already probing and exploiting unpatched NetScaler appliances.
- No Workarounds: Citrix does not recommend any mitigation other than upgrading to the fixed builds.
- Threat Surface: Exploits can lead to network intrusion, lateral movement, and session hijacking—even bypassing authentication in some cases.
How to Patch: Practical Steps
- Upgrade Affected Devices:
- Update to 14.1-47.48 or later for branch 14.1.
- Upgrade to 13.1-59.22 or later for branch 13.1 and equivalent FIPS/NDcPP versions.
- Patch Management Interface:
Ensure all Management Interface deployments are updated. - Check Gateway/AAA Deployments:
Patching is especially urgent for appliances used as Gateway or AAA virtual server. - Monitor Security Advisories:
Stay alert to further updates and threat indicators issued by Citrix.
Final Recommendations
Organizations that delay patching face immediate risk of compromise, including data theft and unauthorized access to internal infrastructure. Cybersecurity teams are urged to patch all NetScaler ADC and Gateway appliances as soon as possible and validate the integrity of affected systems post-upgrade.
Take proactive steps today—protect your infrastructure and maintain vigilance for related updates from Citrix.




