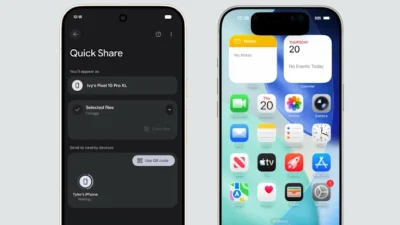
ThreatsDay Bulletin: Wi-Fi Hack, npm Worm, DeFi Theft, Phishing Blasts— and 15 More Stories
Think your Wi-Fi is safe? Your coding tools? Or even your favorite financial apps? This week proves again how hackers, companies, and governments are all …

![5 Threats That Reshaped Web Security This Year [2025]](https://x86.se/wp-content/uploads/2025/12/5-threats-that-reshaped-web-security-this-year-2025-400x225.webp)